Beware of Crypto-Stealing Malware Installed During Zoom Calls

While cryptoasset scammers are increasingly trying to lure their victims onto fake video call platforms to install malware via malicious links, calls on established platforms such as Zoom can also come with the risk of losing your cryptoassets, as a recent case demonstrates.
An X user, Jake (@jakegallen_), CEO of NFT and AI projects such as Emblem Vault and Agent Hustle, shared his story of how a Zoom call cost him more than $100,000 in cryptoassets such as bitcoin (BTC), ethereum (ETH), and NFTs. Moreover, according to the victim, criminals were also able to log into his X, Gmail, and other accounts.
According to Jake, the criminals used the so-called Elusive Comet tactic, which allows threat actors to take advantage of a loophole in Zoom settings that grants access to a victim's computer and allows them to install malware—in this case, Goopdate.
The setting in question is called "Remote access" and is activated by default. It lets the host of the call access your computer.
"This means you probably have this feature on RIGHT NOW. The crazy part is that it is also LOCKED, which means only an admin can change it," the victim said, adding that only an external account can be the admin of your own Zoom account.
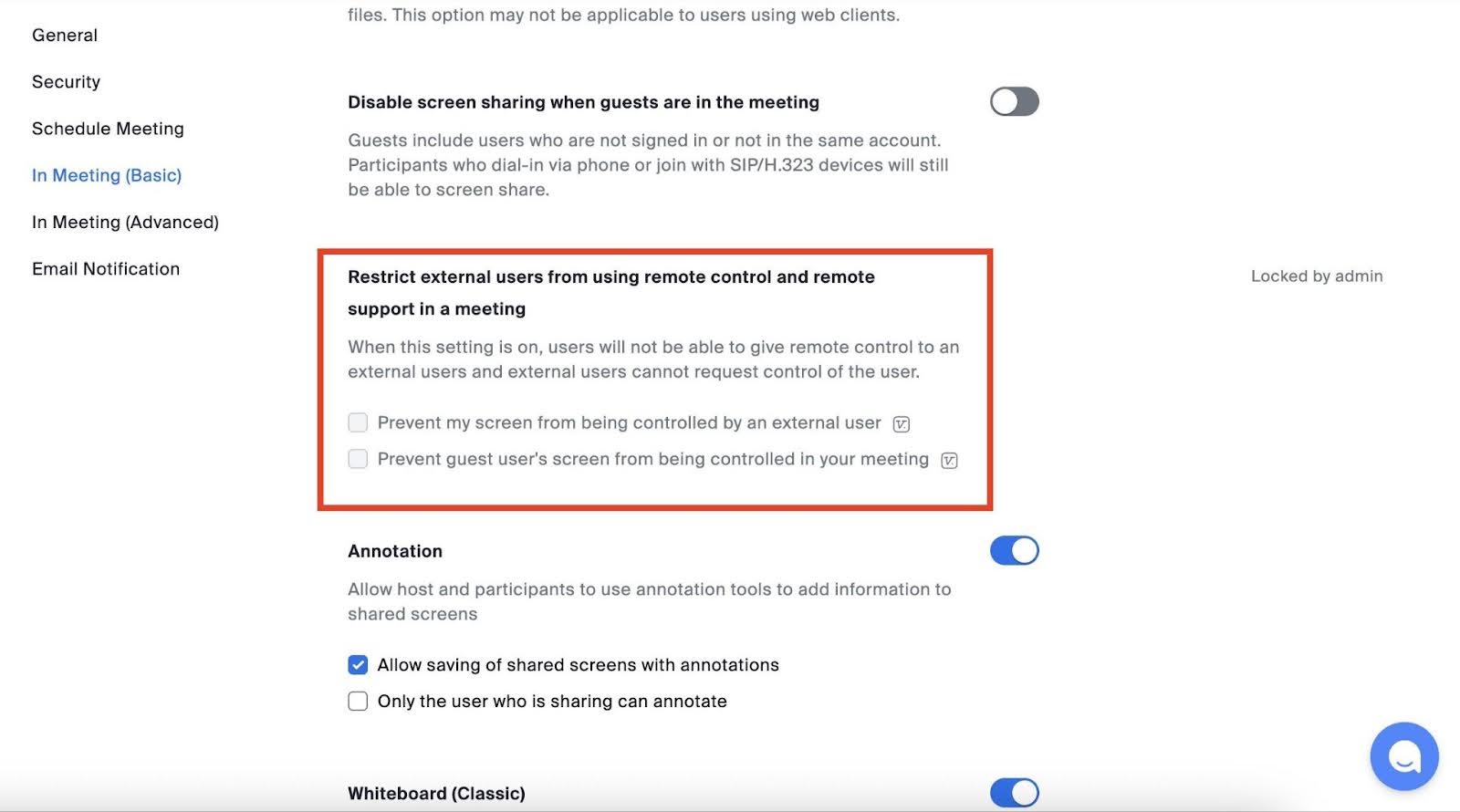
However, according to him, the feature can be turned off in the following way: After you open Zoom settings in your browser (not the desktop app), enter 'Settings,' click on 'Meeting,' and select 'In Meeting (Basic),' where 'Screen Sharing' can be turned off.
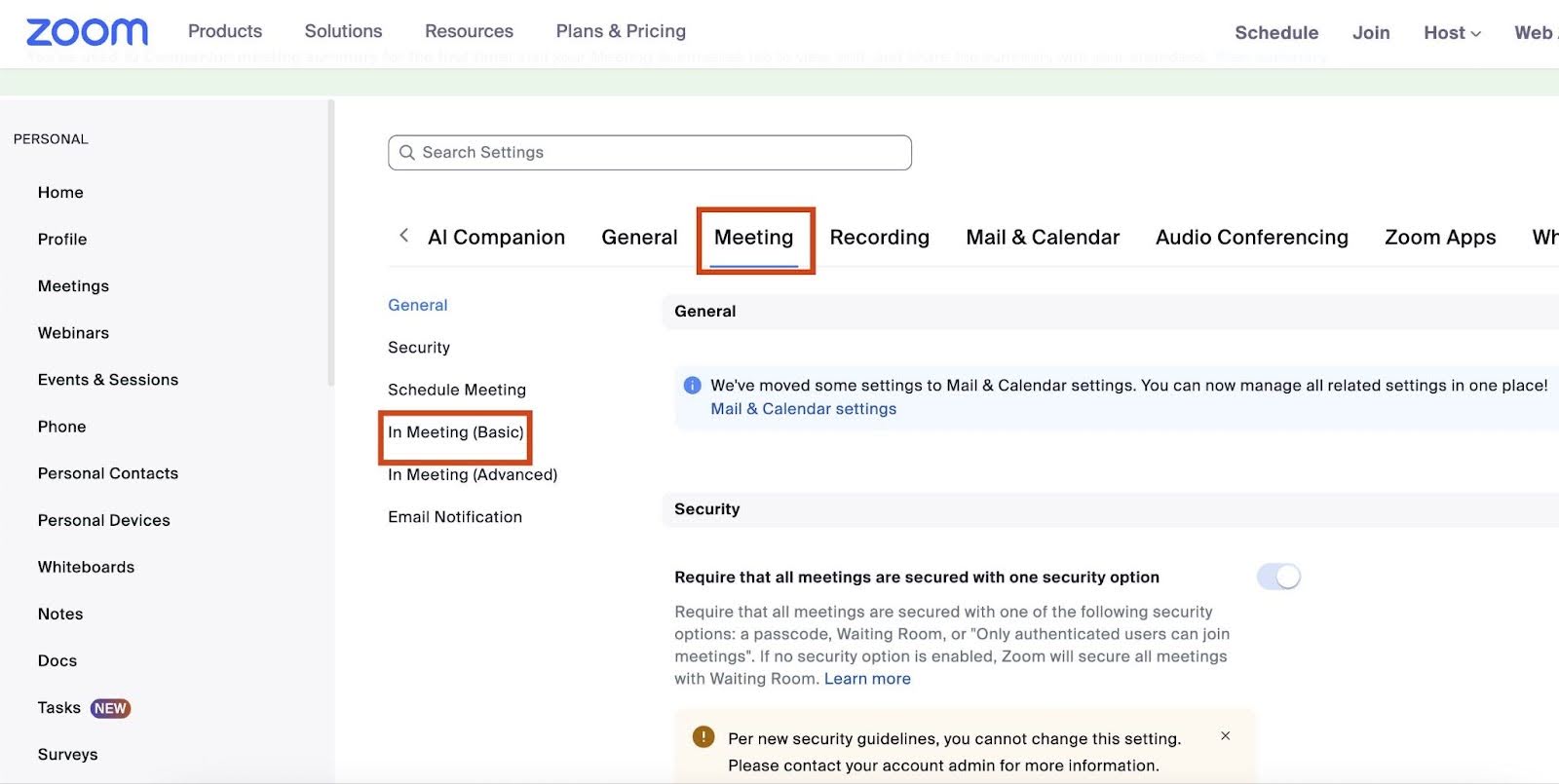
Alternatively, if this feature is on and the host asks to share your screen, they'll be able to "install malware in your computer and have access to any logged-in application, wallet, and saved files."
However, the victim also noted that he doesn't remember clicking a button to give remote access, nor did he see any displays during the call indicating that remote access was granted.
In either case, Jake said he was able to retrieve a malware file from his computer with help from Security Alliance, and the file can now be analyzed by security teams.
Meanwhile, another mystery in this case is how the scammers managed to access Jake's hardware wallet Ledger, where he stored his NFTs.
"As far as the Ledger goes, I'm not too sure how they accessed the wallet. I had only logged in a few times over the 3 years since I set it up, and never wrote the password down anywhere digitally. After review, I don't think it's a Ledger hack but something related to my desktop," Jake said.
In either case, the victim said he's in contact with Zoom.
"I have been told the CEO of Zoom has been made aware of the situation, but I have not been personally contacted by anybody other than through Twitter or email via their official channels," Jake said.