AirAsia Mobile App Vulnerabilities Found as Fraudsters Target Travelers

An analysis of the AirAsia Mobile App revealed multiple poor security and privacy issues and potential vulnerabilities that could have been exploited by fraudsters.
In recent weeks, several stories have emerged from internet users claiming to be AirAsia customers. They reported that after using their payment cards, even virtual ones, to purchase tickets with the major Asian airline, the same cards were used for unauthorized purchases, such as at Walmart. A similar complaint surfaced online as far back as 2016.
On Reddit, this past November, PastDepth9102 said that months after they shared their virtual card data with AirAsia on their iOS app, "[someone] has tried to use that card for purchases [overseas] at Walmart. This [credit card] has never been used anywhere else."
Another user, firealno9, also said they received a card authorization notice from Walmart right after booking an AirAsia flight.
"Had to cancel the card," they added. Another Reddit user complained that they were getting payment requests from "loads of random European travel companies," as their card had only been used with AirAsia.
Posters have also shared alleged screenshots showcasing potential fraud.
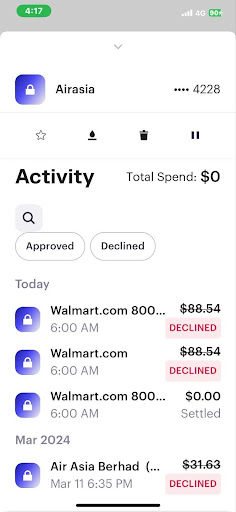
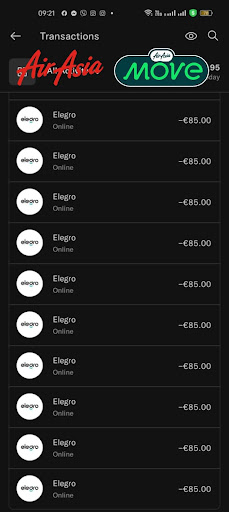
We tested the AirAsia app by doing a static analysis and identified several security and privacy issues that show poor practices of the app.
Weak points were uncovered during the analysis of excessive permissions, poor data privacy handling, cryptographic practices, binary protection, and more.
Here’s a more detailed breakdown.
Check Your Permissions
The analysis revealed that the app requests excessive permissions such as READ_PHONE_STATE, which could be exploited to gather sensitive data like device identifiers. Other potentially dangerous permissions include access to location, camera, microphone, and contacts. It’s important to review the permissions granted to this app—or any app you use.
Top Dangerous Permissions 17 (permissions that are widely abused by known malware)
android.permission.INTERNET,
android.permission.RECEIVE_BOOT_COMPLETED,
android.permission.ACCESS_WIFI_STATE,
android.permission.ACCESS_NETWORK_STATE,
android.permission.WRITE_EXTERNAL_STORAGE,
android.permission.READ_PHONE_STATE,
android.permission.GET_TASKS,
android.permission.WRITE_SETTINGS,
android.permission.RECORD_AUDIO,
android.permission.ACCESS_FINE_LOCATION,
android.permission.ACCESS_COARSE_LOCATION,
android.permission.CAMERA,
android.permission.VIBRATE,
android.permission.READ_CONTACTS,
android.permission.GET_ACCOUNTS,
android.permission.READ_EXTERNAL_STORAGE,
android.permission.WAKE_LOCK
Other Common Permissions 10
android.permission.CHANGE_NETWORK_STATE,
android.permission.MODIFY_AUDIO_SETTINGS,
android.permission.ACCESS_BACKGROUND_LOCATION,
android.permission.READ_CALENDAR,
android.permission.FLASHLIGHT,
android.permission.FOREGROUND_SERVICE,
com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE,
android.permission.BLUETOOTH,
android.permission.CHANGE_WIFI_STATE,
com.google.android.c2dm.permission.RECEIVE
Poor Security Practices
Static analysis of the AirAsia mobile application reveals several poor security practices and vulnerabilities that expose sensitive user data and weaken the app's overall security posture. Key issues include logging sensitive information, insecure WebView implementations, and the use of outdated or weak cryptographic algorithms such as MD5, SHA-1, and ECB mode encryption. Furthermore, the app demonstrates insecure handling of data storage, with world-readable and writable permissions on certain files, which could lead to unauthorized access or modification by malicious applications. The presence of hardcoded sensitive information and the use of insecure random number generators also increase the risk of exploitation. These issues highlight the importance of adhering to secure coding standards, such as those outlined in the OWASP Mobile Application Security Verification Standard (MASVS), to ensure robust protection against potential threats. Addressing these vulnerabilities should be a top priority to safeguard user data and maintain trust in the application.
Unsecured Data and Poor Cryptographic Practices
Another vulnerability stems from missing or improperly configured assetlinks.json files for App Links, which could expose travelers to phishing attacks. This makes users susceptible to clicking on fake websites and inadvertently sharing sensitive data with fraudsters. Additionally, while the app implements Network Security Configuration, it is not comprehensive.
The app is also vulnerable to the Janus exploit on certain Android versions, enabling attackers to modify the app undetected. Furthermore, the app can be installed on outdated Android versions that no longer receive security updates, and its binary protection is insufficient, potentially allowing attackers to execute malicious code.
Analysis of dangerous permissions and components
| Category | Count | Percentage (%) |
|---|---|---|
| Total Permissions | 69 | 100 |
| Dangerous Permissions | 17 | 24.6 |
| Exported Components | 35 | 100 |
| High Severity Issues | 5 | 11.6 |
| Medium Severity Issues | 15 | 34.9 |
This isn’t the first time the airline has faced security issues. Two years ago, the personal data of 5 million users was leaked. More recently, in December, Thai media reported issues with the AirAsia MOVE Thailand app, alleging it allowed users to purchase non-existent flight tickets. The company blamed a third-party provider responsible for the app. Meanwhile, social media users suspect the AirAsia MOVE app or the airline’s payment system may be linked to the latest payment card fraud incidents.
AirAsia itself has not made any public statements regarding these customer complaints.
In a January post, AirAsia claimed it "observes the highest standards in handling data, safety, and security" and uses "data encryption to safeguard users’ information."
We have contacted the airline for comment and will update this story if they respond.
How Can You Protect Yourself?
If you’re an AirAsia customer, consider these measures to protect yourself from potential financial losses:
- Block Cards: If you’ve previously used a physical or virtual card with AirAsia, block the card and request a new one.
- Use Virtual Cards: For future transactions with AirAsia, use single-use virtual cards.
- Monitor Transactions: Regularly review your bank statements for unauthorized activity.
- Stay Updated: Follow legitimate sources for updates on AirAsia’s security measures
Additionally, these general precautions can help you stay safe when using any app:
- Keep Your Device Updated: Use a device with the latest Android or iOS version for better security.
- Review Permissions: Periodically check and limit app permissions in your phone’s settings.
- Stay Vigilant Against Phishing: Avoid clicking on suspicious links, and double-check URLs even if they appear coming from a legitimate source.