Alibaba, an Open Authenticated MySQL Server Targeted by Security Researcher? Or Data Extortionist?
Recently, I discovered an interesting data breach, purportedly reported to Alibaba (US) Technology Co., Ltd by a security researcher from Sweden. However, the more I analyzed the message left by this so-called 'Good Samaritan,' the more questions it raised than it answered.
The compromised MySQL server appears to be hosted within a San Jose-based data center operated by Alibaba (US) Technology Co., Ltd., which operates as a key U.S. node within Alibaba Cloud’s global infrastructure. Additionally, there was no indication when the incident occurred.
According to vulnerability indicators noted by an IoT (Internet of Things) search engine, the MySQL server had no security measures in place whatsoever, reminiscent of the lax security practices of the late 1980s. Accessing the database required no username or password, conjuring one of those Hollywood-style “press one key and you’re in” scenes.
With their database completely exposed to the public, a ransom note was found within the dataset, planted there by the attackers, informing the company that the server had been compromised and the contents of the server exfiltrated.
The ransom note included a Bitcoin wallet address, a ransom demand of 0.1 Bitcoin (BTC), equivalent to $108,048.70 USD at the time of writing, and a disposable Mailinator email address.
With such little information to go by, I decided to run a quick search for the wallet address revealed that it is registered on two blockchains (BTC and BCH), but neither shows any transaction history.
Breaking down the narrative
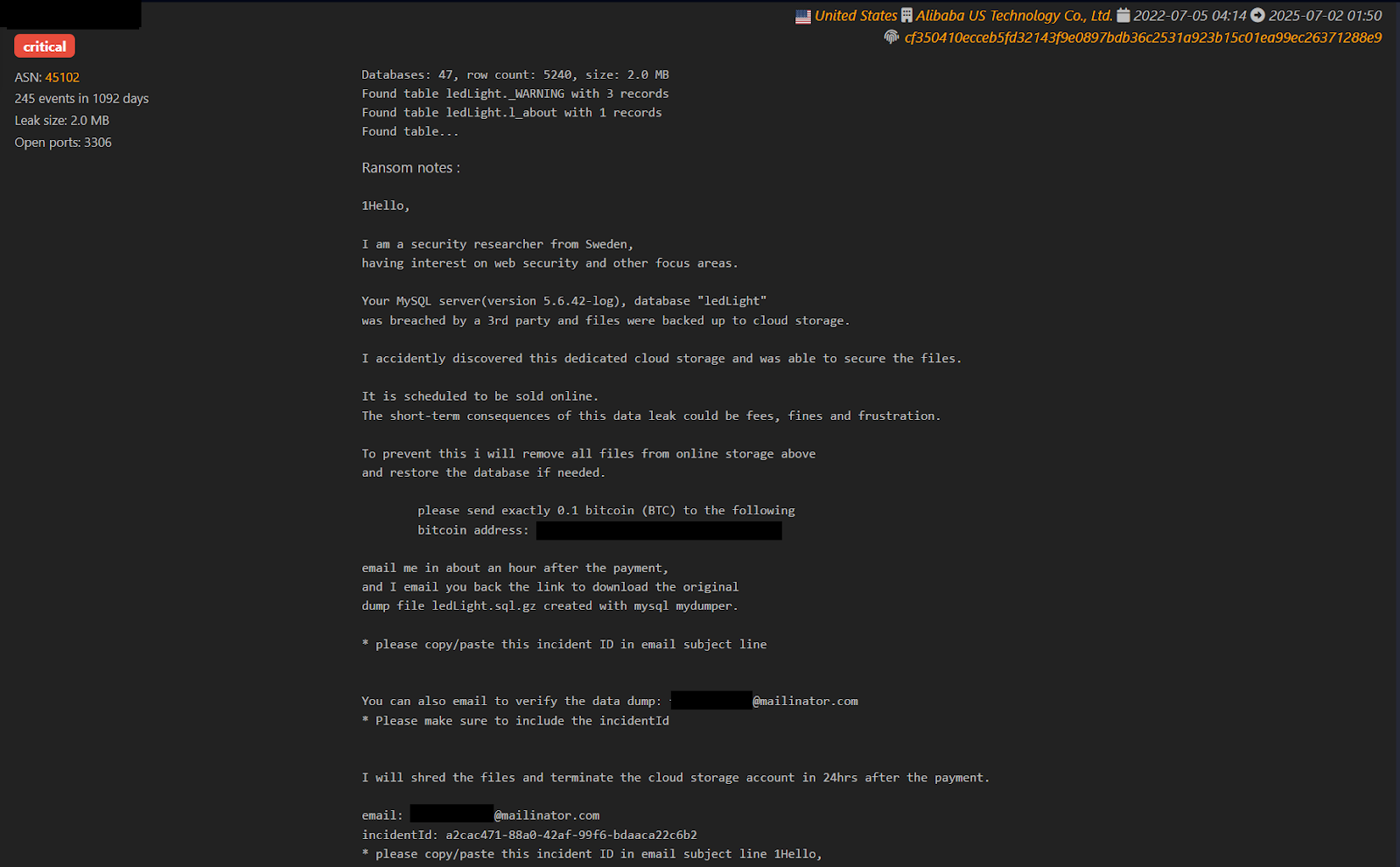
In the above screen capture is a prime example of what a secure disclosure should not look like. As you continue reading, you will see why.
The image contains a message that was sent to Alibaba’s data servers in San Jose, by someone purporting to be a security researcher from Sweden. How it was sent, whether it was slipped in the MySQL dataset, or by email is not indicated.
1Hello,
I am a security researcher from Sweden, having interest on web security and other focus areas.
Your MySQL server(version 5.6.42-log), database "ledLight"
was breached by a 3rd party and files were backed up to cloud storage.
I accidently discovered this dedicated cloud storage and was able to secure the files.
It is scheduled to be sold online.
The short-term consequences of this data leak could be fees, fines and frustration.
To prevent this i will remove all files from online storage above and restore the database if needed.
please send exactly 0.1 bitcoin (BTC) to the following bitcoin address:
[REDACTED]
email me in about an hour after the payment,
and I email you back the link to download the original dump file ledLight.sql.gz created with mysql mydumper.
* please copy/paste this incident ID in email subject line
You can also email to verify the data dump: [REDACTED]@mailinator.com
*Please make sure to include the incidentId
I will shred the files and terminate the cloud storage account in 24hrs after the payment.
email: [REDACTED]@mailinator.com
incidentId: a2cac471-88a0-42af-99f6-bdaaca22c6b2
* please copy/paste this incident ID in email subject line
You can also email to verify the data dump: [REDACTED]@mailinator.com
* Please make sure to include the incidentId
There are several things wrong with this message. Both the message from the so-called “security researcher” and the ransom note contain identical errors and syntactic patterns, strongly indicating that they were authored by the same individual. Also, both exhibit clear signs of poor English grammar and language proficiency.
Aside from this analysis, it is unusual for someone pursuing a responsible vulnerability disclosure to provide so little information about where the breach was allegedly discovered or who may have been responsible, beyond vaguely attributing it to a “third party.”
Instead, the individual placed greater emphasis on how to pay the ransom, offering detailed instructions on where and how to send the payment.
It’s kind of a no-brainer.