An Emerging RaaS: FunkSec
The landscape of cybercrime continues to evolve, with threat actors not only targeting personal sensitive information but also business ideas. These malicious groups are increasingly adopting business-like structures to maximize profits. One of the key advancements in this regard was the initiation of the Ransomware-as-a-Service (RaaS) model, which has opened the door to non-technical individuals, enabling their participation in cybercrime. This shift has led to a significant surge in ransomware activities, with new groups emerging almost daily. Among these is FunkSec, a ransomware and extortion group discovered in December 2024.
FunkSec Overview
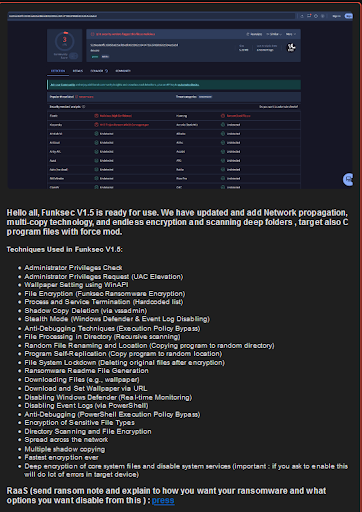
Despite being a relatively new player, FunkSec has already demonstrated a significant impact across various industries, including the public sector, energy, manufacturing, media, IT, and education. The group operates a Tor-based data leak site (DLS), centralizing its ransomware activities. Additionally, they promote a free DDoS tool and have updated the version of their RaaS software —FunkSec V1.5. Details about their ransomware tool, FunkSec/FunkLocker, are available on platforms like PCRisk.
Impact and Reach
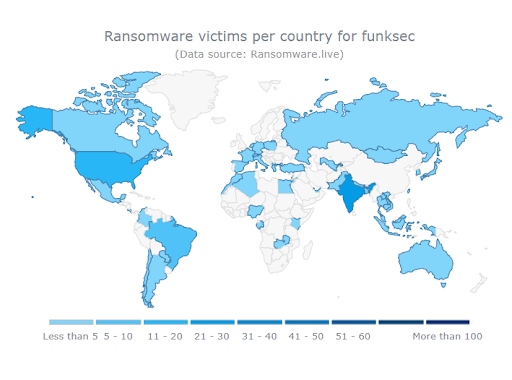
As of January 26, 2025, FunkSec has claimed 134 victims globally. These victims span multiple countries, including the United States, India, Brazil, Spain, Indonesia, and Bangladesh. The group’s rapid spread and diverse target base include Asian and African countries, in addition to Western nations. In an interview with Osint10x, the group claimed that their main targets were the United States, India, and Israel. Data shows they attacked the United States 20 times, India 21 times, and Israel 4 times. In the same interview, the group admitted that AI contributes to 20% of their operations and that they have developed their own proprietary AI tool, WormGPT.
Funksec made headlines late last week for a joint attack with Fsociety on the Punjab Government website.
How to Protect Against Ransomware
To reduce the risk of ransomware:
- Regular Backups: Keep offline or secure cloud backups and test restoration regularly.
- Endpoint Protection: Use antivirus and EDR tools to block threats.
- Patch Systems: Keep software and devices updated to close vulnerabilities.
- Segment Networks: Limit access to sensitive data to reduce ransomware spread.
- Employee Training: Educate on phishing and cybersecurity best practices.
- Email Security: Filter out malicious attachments and links.
- Access Controls: Use strong passwords and enable multi-factor authentication (MFA).
- Incident Response: Have a response plan ready to minimize damage.