Entech Engineering, Inc., Recently Targeted By INC Ransom
Just today, the double-extortion group known as INC Ransom claimed another victim: the U.S.-based engineering consulting firm Entech Engineering, headquartered in Reading, Pennsylvania.
Among the 50 screenshots leaked by the ransom group, they offered a rather enthusiastic description of their haul, saying, “We downloaded a lot of important information: projects, budgets, information about partners Entech Engineering, Inc.! In the screenshots, only a small part of what we have!”
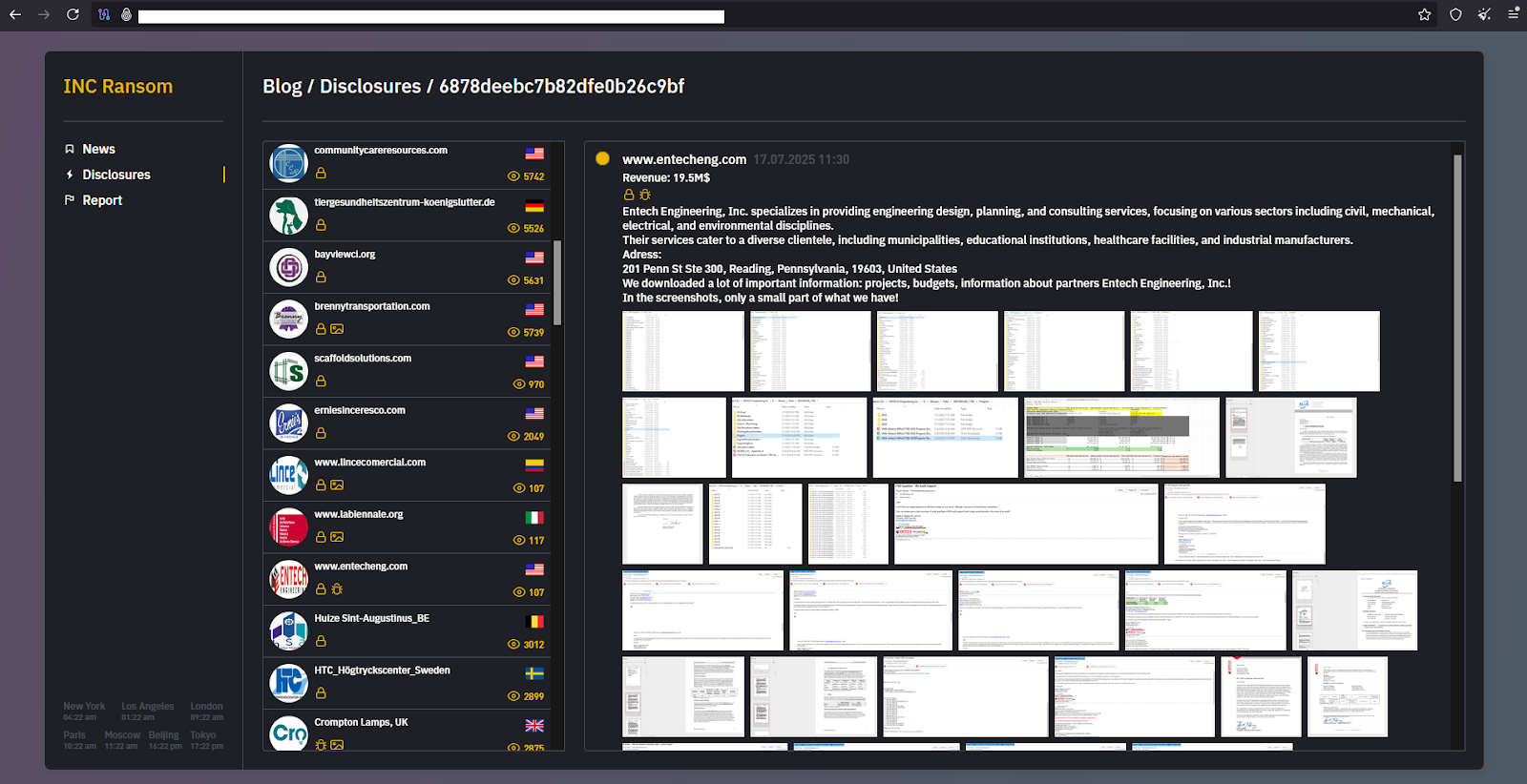
Several of the screenshots suggest that the attackers gained access to Entech Engineering’s internal shared drive, 857 GB comprising 747,698 files across 49,840 folders, and encrypted its contents.
While the leak is labeled as an Active Directory dump, the screenshots appear to show only access to the shared drive. If the group was able to pivot further across the network, they did not disclose it. The initial attack vector remains unconfirmed.
The screenshots show internal emails, financial records, safety data sheets, and other internal documents, including PII (personal identifiable information). INC Ransom marked the files as encrypted.
Additionally, there does not appear to be a countdown or a deadline for the company to pay published on their Tor site.
How the Attackers Gained Access
Analyzing how the group gains access can only offer some insight. For example, INC Ransom is known to source credentials from InfoStealer malware logs, often purchased on Russian-speaking forums on dark web markets. This is ostensibly the case here.
It is not uncommon for Engineering Firms to rely on VPNs or RDP for remote work. Therefore, if any employee, contractor, or any third-party reused passwords or was compromised, these logins could have been harvested months earlier.
Furthermore, ransom groups often rely on deceptive categorization by mislabeling leaks as “Active Directory dumps” when the data was from shared drives or mail servers, a tactic used to intimidate and inflate perceived access.
In the case of Entech Engineering, the group labeled the leak as an "Active Directory dump" on their Tor site. However, screenshots suggest the attackers had access only to the internal shared drive, not the AD database itself, potentially a psychological tactic to inflate the perceived depth of the breach.
Who is INC Ransom
Like other groups, INC Ransom (also known as INC, or INC Ransomware Group) is a double-extortion ransomware gang that made its first appearance in mid-2023 and has maintained active ransomware campaigns since.
The group operates a RaaS model and primarily targets organizations in North America, Europe, and parts of Asia, with a particular focus on sectors such as healthcare, education, engineering, finance, and manufacturing.
Currently, there have been no verified public attributions of the ransomware group to any specific country. However, based on certain behavioral patterns, infrastructure, and their proximity to Russian-speaking dark web markets, cybersecurity experts believe the group operates out of a Russian-speaking country.