How Ransomware Gangs Choose Their Targets and Profit

Some years ago, I watched a young hacker sitting at a laptop as he wrote an undetectable ransomware script in Python from memory, right in front of me. He tested it, and it seamlessly encrypted the files in the container where he had sandboxed the malware.
Regardless of how sophisticated their methods may be, whether by developing custom malware strains or relying on off-the-shelf tools paired with advanced social engineering, most threat actor groups are still seeking easy targets, even if those targets appear completely random.
Despite the random targeting, each has something in common: the targets are usually businesses. This means every place of commerce is a potential target in the game of cyber Russian Roulette.
The Art of Vulnerability
Most hackers today don’t completely rely on the old legacy method of host discovery by scanning huge IP netblocks for open ports, which can trigger security events and raise red flags, although this method is still useful in certain circumstances.
When it comes to legitimate security auditing and vulnerability indexing tools like Shodan and LeakIX, their existence serves as a double-edged sword. In earlier generations, hackers almost exclusively built their own toolkits, whereas today, we often weaponize tools created by the cybersecurity industry itself.
Tools like Shodan allow some of the most prolific cybercrime groups to search the internet for vulnerable devices to exploit. For example, a popular target software is the MySQL server.
A threat actor can search port:3306 product:MySQL "authentication disabled" and immediately return search results showing MySQL servers where authentication is disabled, meaning anyone can log in to the server.
By running a search for VNC servers with open authentication using the query ("authentication disabled" port:5900,5901 "RFB 003.008"), you’ll find 2,356 vulnerable devices at the time of this writing.
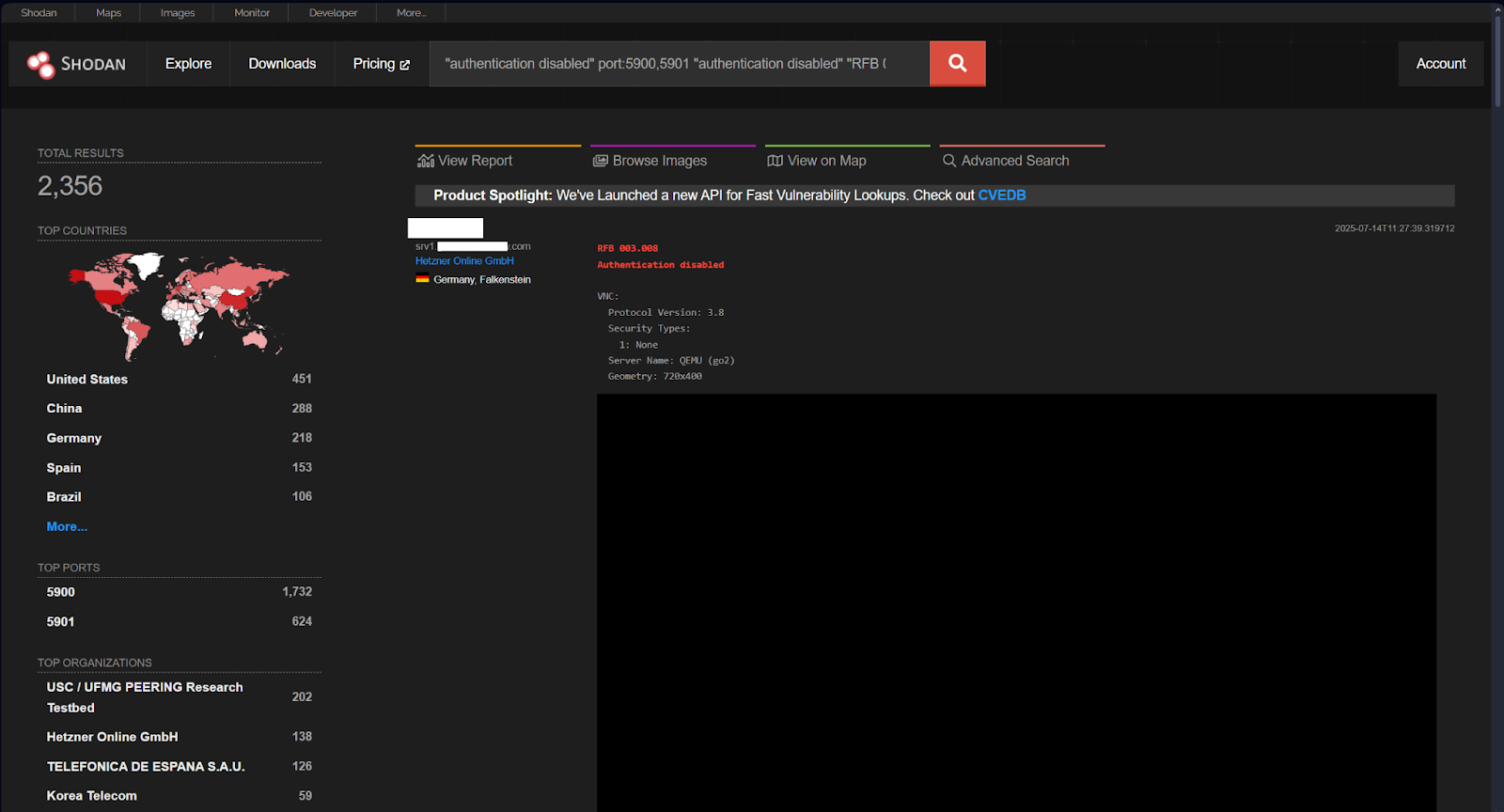
Whether hackers are looking for poor authentication or easily exploitable vulnerabilities to gain access to servers, in each instance, companies have shown very little security posture.
This is how they end up victims.
Let me emphasize this point: it's not simply because their network devices and any potential vulnerabilities are indexed by specialized search engines, but because many of the companies that fall victim fail to maintain those systems, despite the clear dangers of the security landscape we all live in.
Here is a perfect example of a hosting service in France that fell victim to a ransomware attack, simply because their MySQL server required no credentials to access the database:
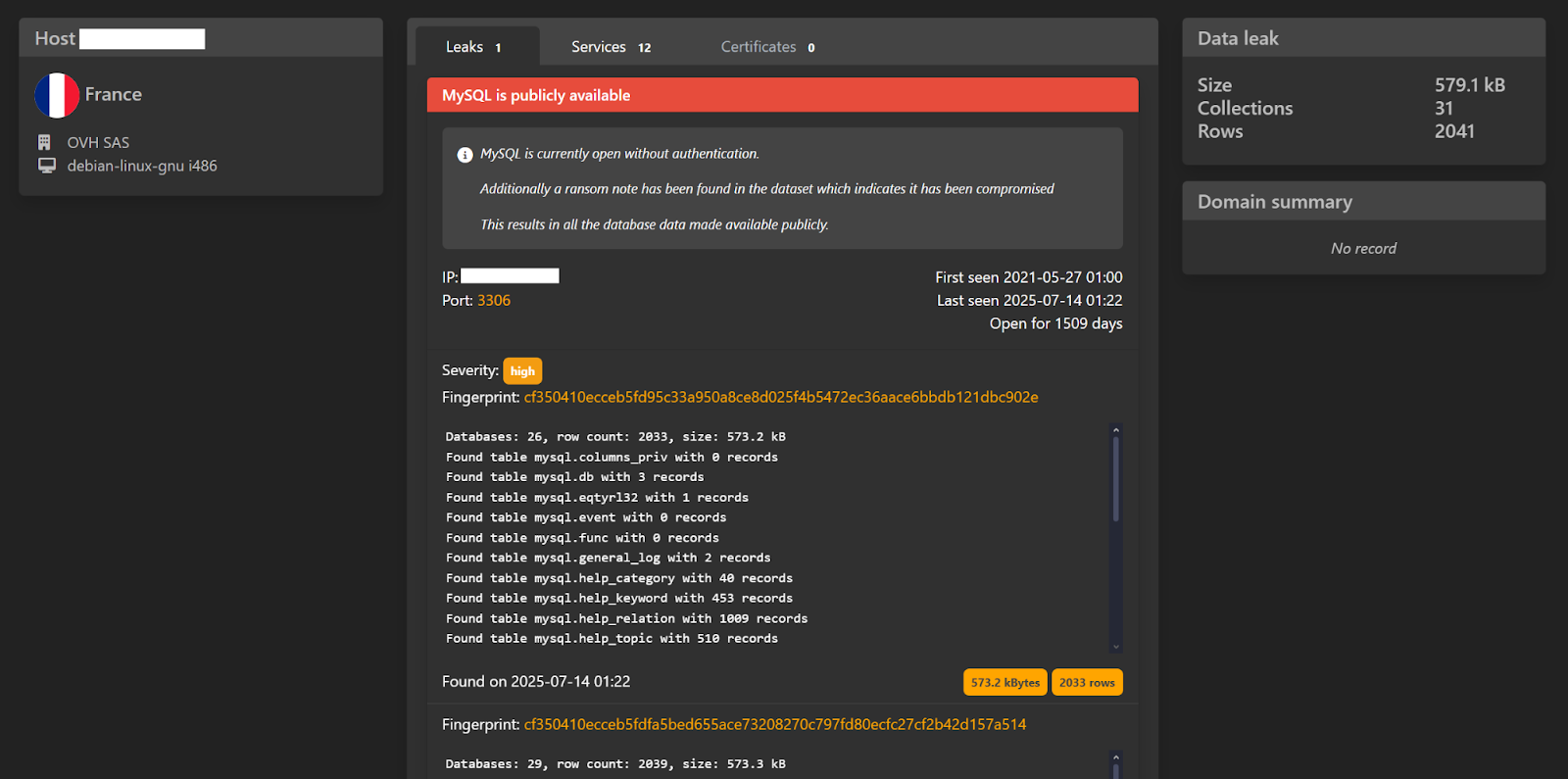
Lastly, because companies are seemingly willing to cut corners by not maintaining the security integrity of their systems, as shown in the example below, ransomware gangs find easy targets and hold those systems hostage until their demands are met.
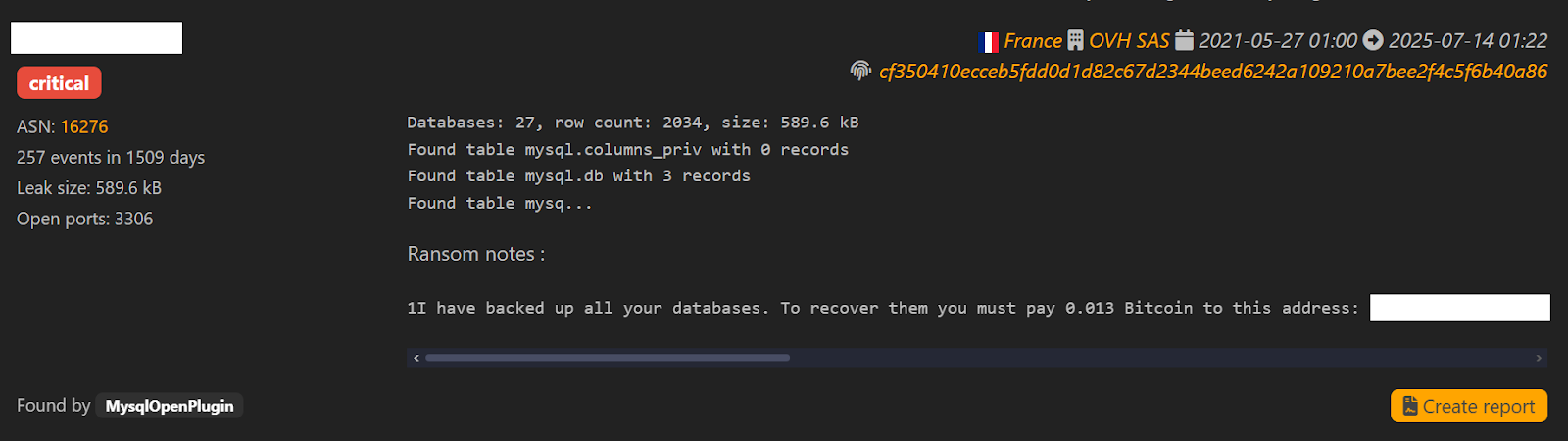
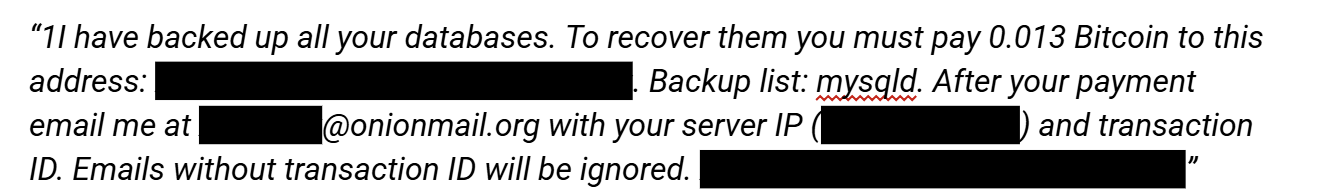
Having a Security Posture Can Reduce Risks of Attack
These methods aren’t necessarily sophisticated. Even using open-source tools like SQLMap makes it relatively simple to exploit known vulnerabilities in MySQL servers, allowing attackers to write data to the server, dump entire databases, and retrieve sensitive files, which are often used as leverage in extortion campaigns.
The way easily accessible tools like this are designed does not require knowledge of databases at all, especially since there’s an overwhelming amount of free tutorials online showing each step in the attack process.
Many of these tools and techniques are openly shared online, often by well-known ethical hackers and cybersecurity experts, fully aware that even the most amateur cybercriminals will be learning from them.
Whatever the case may be, when companies turn a blind eye to insecure environments, they provide the perfect opportunity for cybercriminals to target low-hanging fruit, steal data, and demand a ransom. All of this could be easily avoided with routine security audits to ensure a company’s digital assets are protected in the event of such incidents.
It’s the year 2025, and while security and the means to exploit security are advancing, human nature remains the same.