Infostealer Malware: Protect Your Passwords Before They’re Stolen

Years ago, in my youth as a threat actor, I approached a job search kiosk at a local supermarket. The desktop had virtually no access controls, nothing was locked down, and users could freely explore the system.
The job application form had auto-fill enabled, which allowed me to retrieve the personally identifiable information (PII) of every single applicant. Furthermore, because people misused the kiosk to log into their accounts, such as Gmail and Facebook, I could easily access those accounts, as their credentials were cached in the browser.
Twenty years later, this remains one of the primary reasons why both users and businesses continue to fall prey to cyberthreats, especially to Infostealer malware.
No matter how you slice it, there’s more than one way to find yourself at the receiving end of a cyberattack. Discovering how your cybersecurity posture stands against probing hackers is only half the battle, but it's a lot easier than having to deal with the fallout of a ransomware attack.
While the attack vectors cybercriminals use vary, infostealer malware is designed to do one thing: prey on the fact that most people exercise poor credential hygiene.
This means Infostealer malware is designed to exploit the very convenience we depend upon daily. It targets features that make our digital lives easier, such as saved passwords, auto-filled forms, and remembered sessions. Every shortcut we take for convenience becomes an opportunity for the adversary, and such has been the downfall for millions of users.
- Passwords stored in the web browser
- Session cookies, so logins can be hijacked without 2FA/MFA
- Autofill data (names, addresses, phone numbers, emails)
- Clipboard contents
- Desktop files
- App configuration files, such as VPNs, Messenger apps, and crypto wallets
Put simply, the longer users rely on antedated, vulnerable credential storage, the more effective a cyberattack will be, and the greater the damage. This is why prevention is a must, and it doesn’t have to cost an arm and a leg, either.
Years ago, in my youth, when I was a threat actor, I approached a job search kiosk at a local supermarket. The desktop had virtually no access controls. This meant nothing was locked down, and users could explore the desktop.
The job application form had auto-fill enabled, which allowed me to retrieve the personal identifying information of every single applicant. Furthermore, because people abused the kiosk to log in to their accounts, like Gmail and Facebook, I could easily log in to their accounts since their logins were cached in the browser.
Twenty years later, this is still the reason why users and businesses alike are falling prey to cyberthreats.
Biometric-Locked Password Managers
Infostealers like Redline or Racoon are designed to scrape browser storage, not password managers or vaults. Therefore, if your credentials aren’t in your browser when cybercriminals start poking around, the malware has nothing to grab.
This means choosing a password manager that fits your needs and adopting secure methods for interacting with it, minimizing the need to type credentials, which can be intercepted by keyloggers or malware.
For example, macOS includes robust security features that support biometric authentication for password manager access. I use fingerprint identification to unlock my vault, eliminating the need to type a master password and reducing my exposure to credential theft.
This significantly reduces the risk of credential theft, but one major attack vector remains. For example, if you're logged into LinkedIn using a biometric authenticator via your password manager, the session itself can still be stolen by infostealer malware as long as you're actively logged in.
To mitigate this, it's vital to log out of accounts when you're not actively using them, which ends the session and invalidates the cookie. One effective way to defend against this kind of attack is to use your browser’s Private or Incognito Mode. This will prevent session cookies from persisting after the browser is closed.
Do not stay logged in. This helps to consolidate your security posture.
Avoid 3rd Party Downloads
A major attack vector that has persisted for decades has been malicious software appearing to come from official sources. Despite this masquerade, it's critical to ensure you check for HTTPS, and watch for typo-squatted domains ike g00gle.com, software-update.net, facebo0k.com, etc.
Avoid like the plague any so-called 3rd-party “mirrors” or download portals purportedly part of official repositories or sites.
You can verify digital signatures on downloaded files easily.
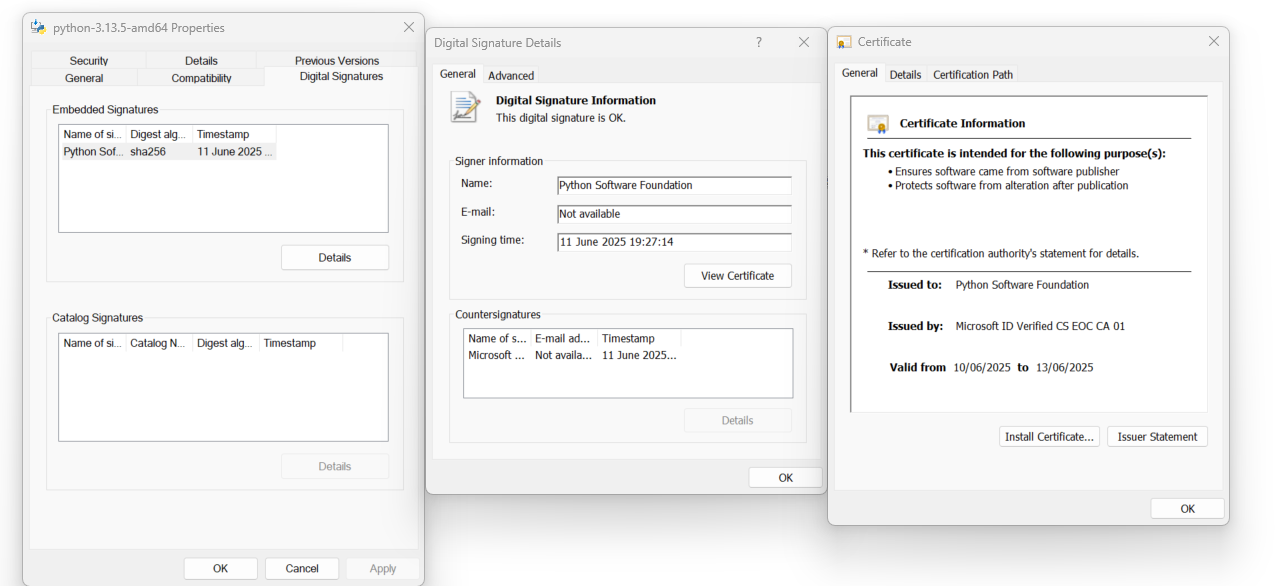
For Windows users:
- Right-click on the file
- Click on Properties
- Click on Details
- Click on View Certificate