KillSec Targets 7 Global Victims: Healthcare, HR, Telematics Hit

KillSec, the RaaS (Ransomware-as-a-Service) group, has been busy recently. According to their leak site on Tor, the list of victims increased, ostensibly overnight, hitting 7 new international targets and exfiltrating data for ransom across multiple sectors.
The group disclosed neither a payment amount nor the contents of the ransom notes. The only information they provided was proof that the breaches had occurred, a brief description of the victim, and individual deadlines.
Screenshots offer a clue as to how the attackers gained access. Our analysis indicates that KillSec did not compromise these companies by exploiting a common software flaw; instead, this appears to be the work of InfoStealer logs. Whether these were acquired from darknet markets or from their own RaaS network.
Nathan & Nathan Human Resources, which is an international human resources firm in the UAE. The firm serves a variety of industries, such as hospitality, construction, healthcare, and technology. They support over 65 businesses and manage HR services for more than 12,000 employees.
The ransomware group posted a deadline of 7 days for Nathan to satisfy their demands for payout. But whether the group will leak the firm’s internal documents is a major risk, regardless of any payout.
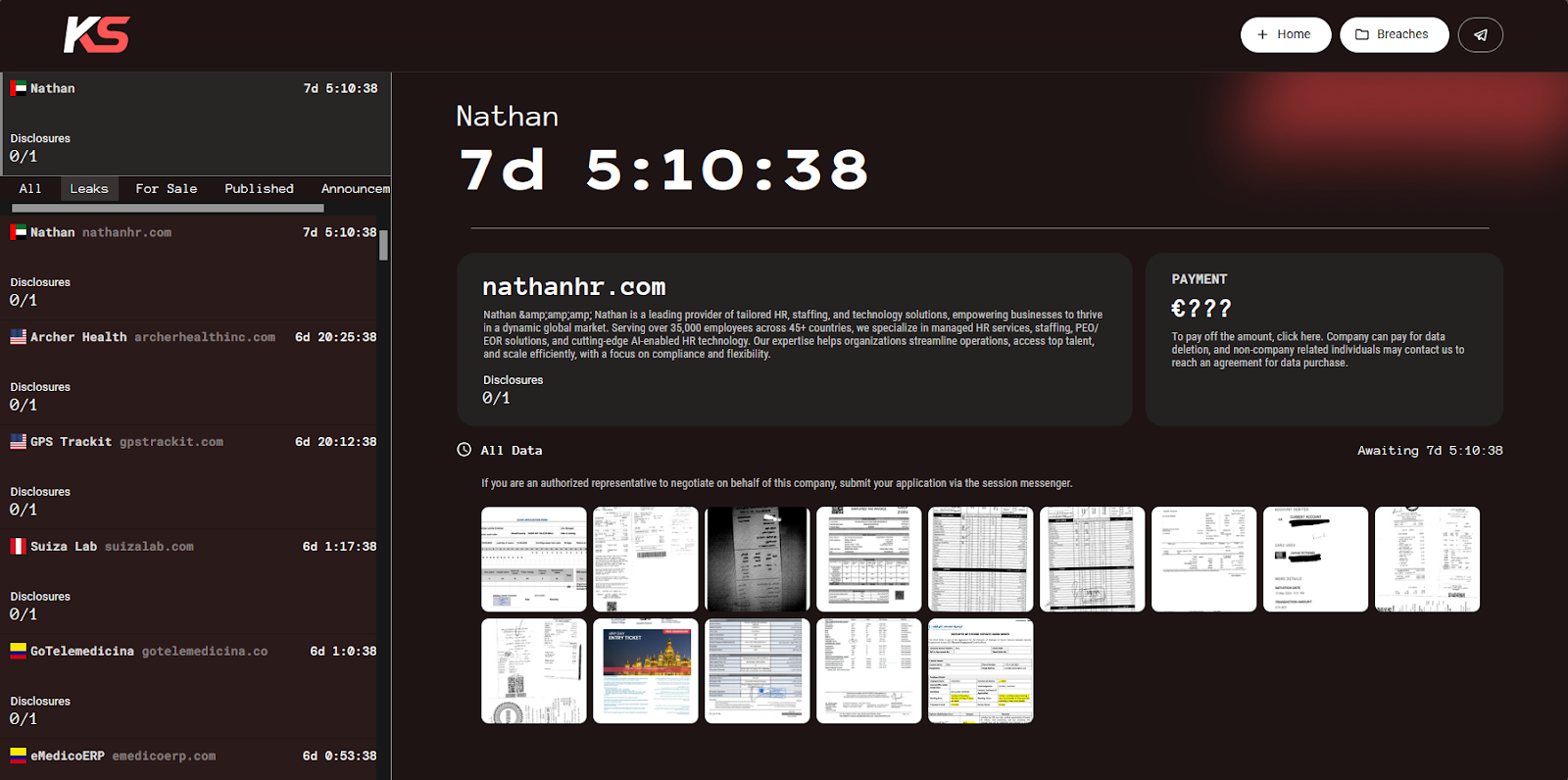
As evidence of the intrusion, the group posted 14 screenshots, which contain the following:
- Laboratory report, containing personally identifying information (PII)
- Sick Leave Certificate, containing medical condition, national ID, and full name.
- POS Bank Slip, containing full name, transaction information, and card reference.
- Leave Application Form, with the employee’s full name, manager, employer details, phone number, and signature.
- Employment Work Order, containing employee identity, HR contact details, and visa/immigration information.
Archer Health
Archer Health, Inc. is a Medicare-certified home health agency based in Carlsbad, California. This company specializes in providing a range of in-home medical services across San Diego and Riverside counties.
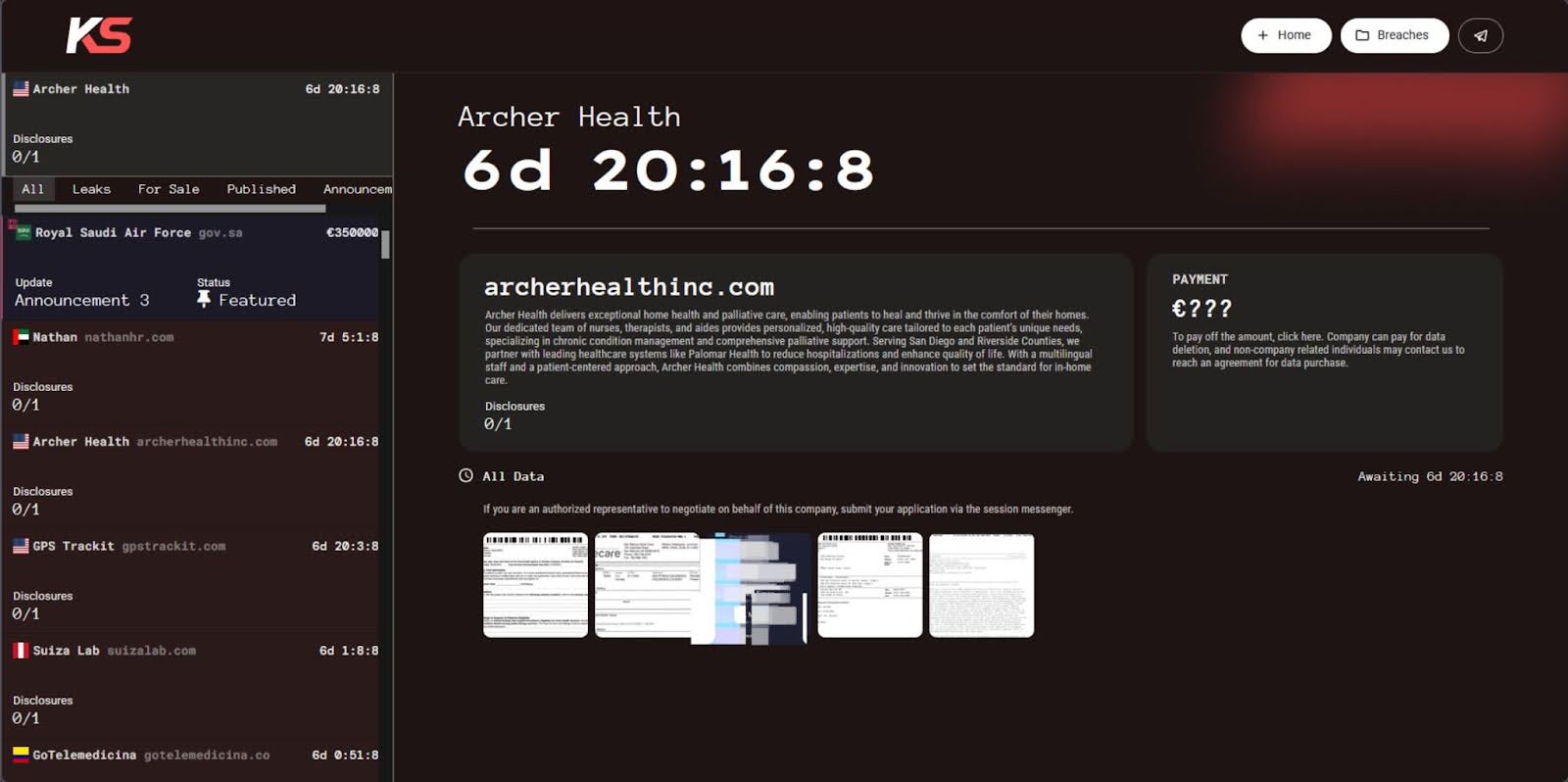
KillSec posted 5 screenshots, containing the full names of multiple individuals, including DOB, healthcare order numbers, and medical documentation context. These also include physician admission notes alongside sensitive patient medical histories and diagnoses. Leaked medical PII always poses a severe risk of identity exposure, theft, and HIPAA-level violations.
Suiza Lab
Suiza Lab S.A.C. is a medical service provider based in Miraflores, Lima, Peru, specializing in a wide range of specialties within the healthcare field. They, too, fell victim to KillSec, who posted 13 screenshots detailing evidence of the data breach.
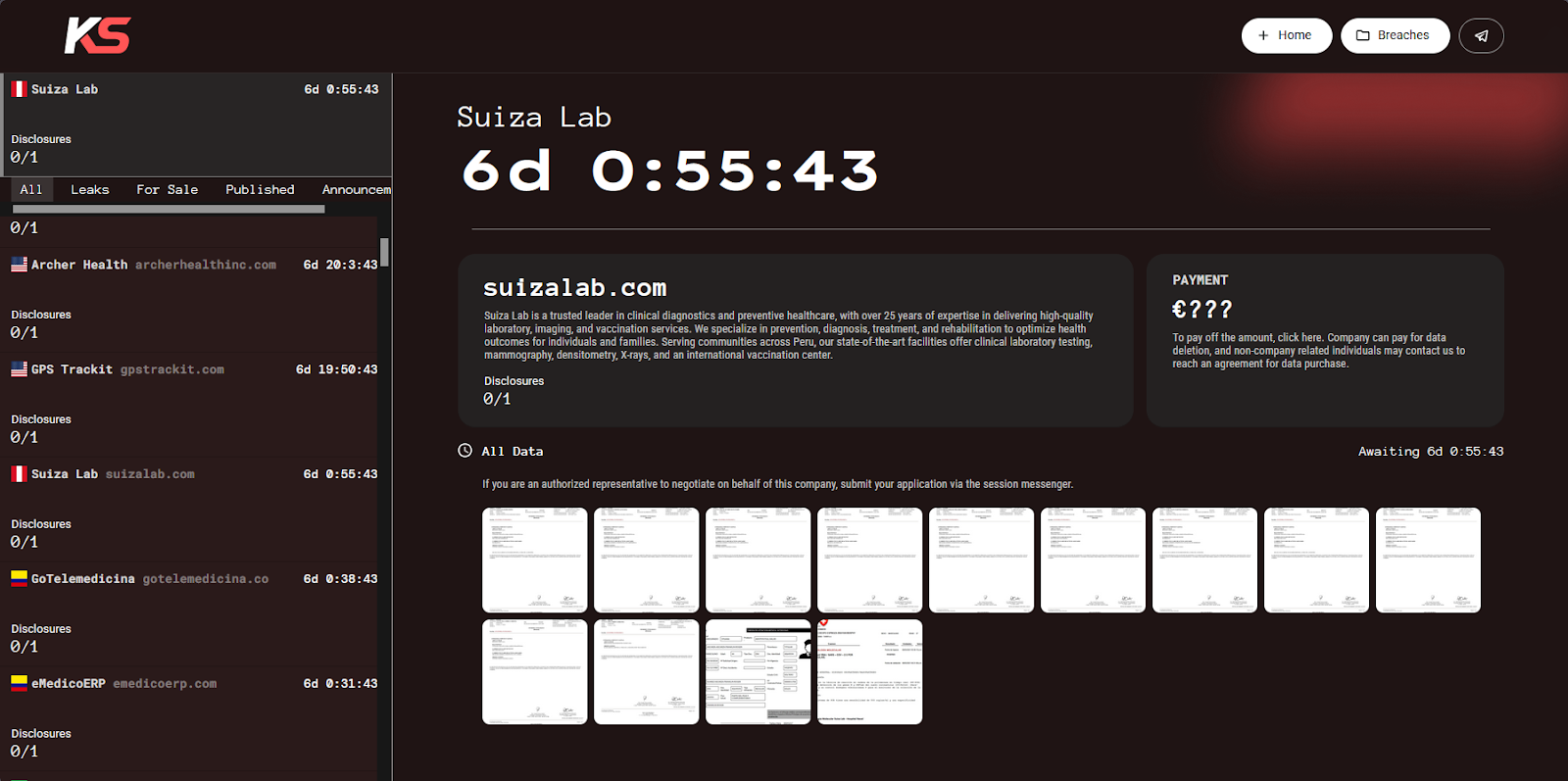
The image reveals medical laboratory reports, specifically cytology reports, containing highly sensitive PII, such as full names of patients, DOBs, laboratory order numbers, diagnoses and test results, doctor names and credentials, and facility information.
MedicSolution+
MedicSolution+ is a medical practice management solution in the form of a digital platform and companion app, aiming to streamline administrative and clinical workflows for the healthcare industry.
KillSec uploaded 17 images, showing proof of some of the data they acquired, which expose a variety of Brazilian medical records, covering histopathology reports (pregnancy tissue analysis), laboratory blood test results, radiology imaging, and a large exposure of patient and medical PII.
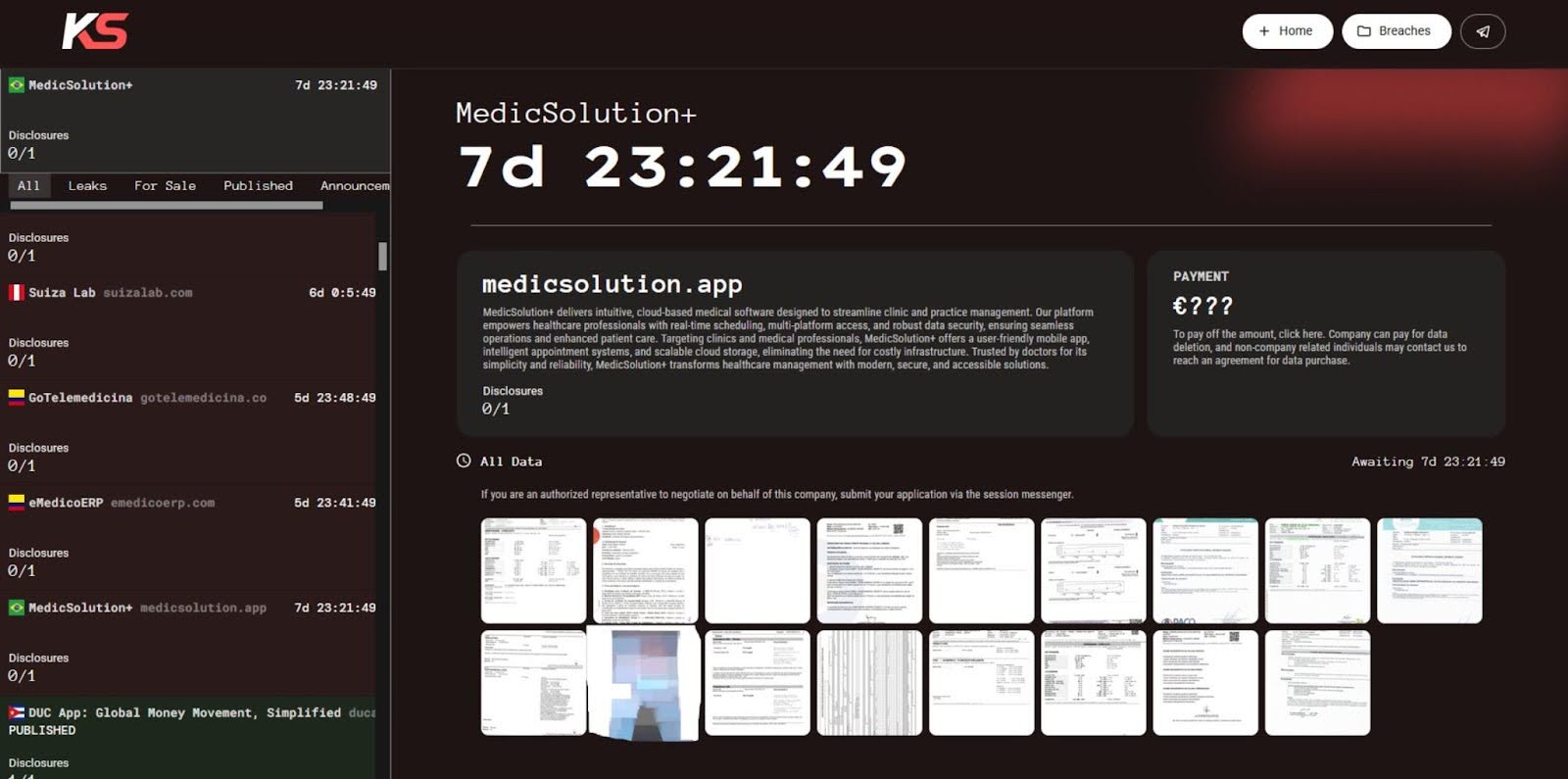
Similar to the data breach above, exposing medical PII protected under Brazil’s General Data Protection Law (LGPD), and if involving international patients, this could also trigger a much broader issue with HIPAA and GDPR.
eMedicoERP
The Enterprise Resource Planning (ERP) software eMedicoERP, developed by DinamicAPPS and designed for healthcare establishments across Colombia, also suffered a critical data breach by KillSec, who leaked 6 screenshots, although one is blank.
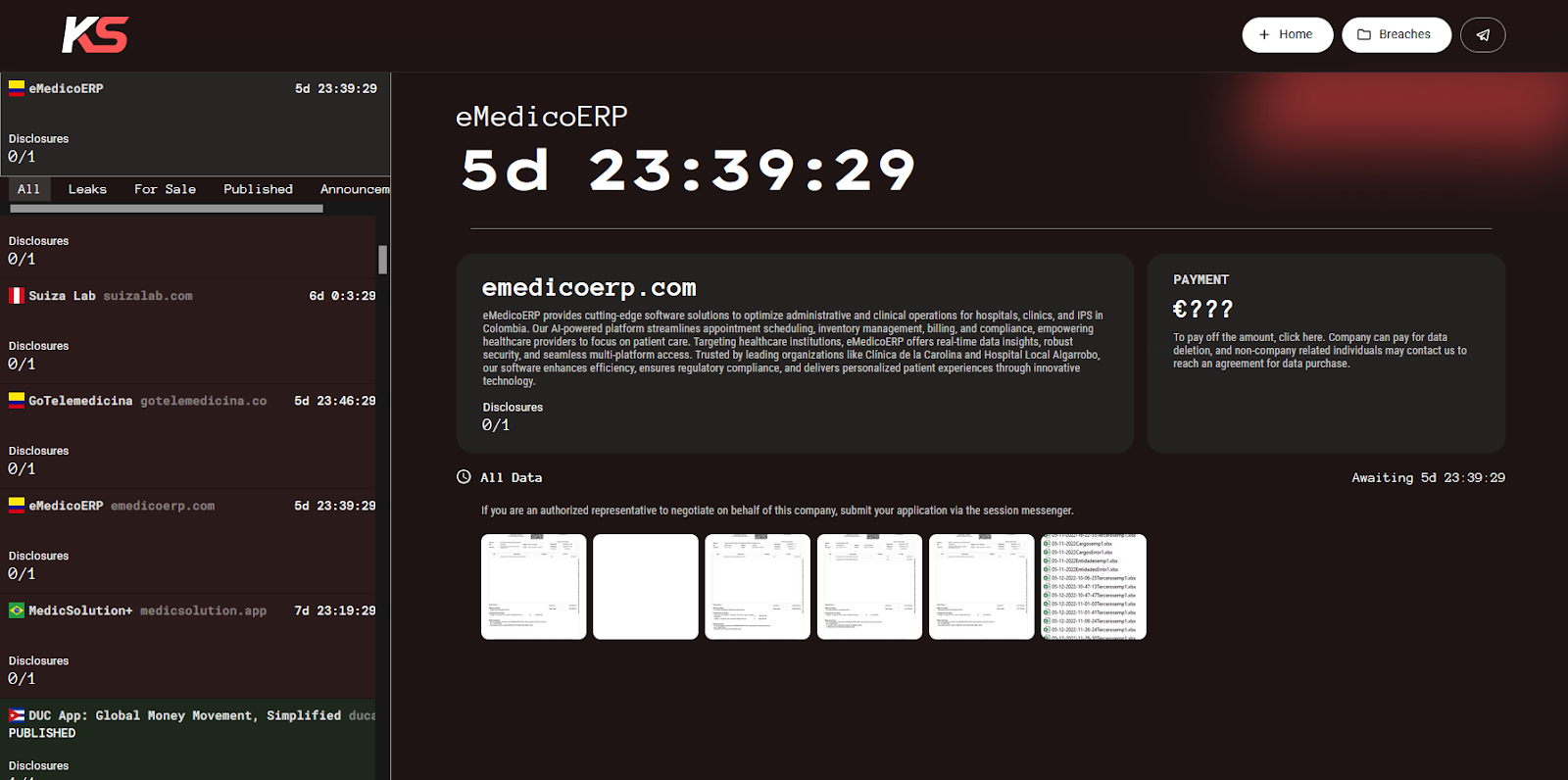
The screenshots contain a variety of contract and financial data, primarily from DinamicAPPS S.A.S., the company behind eMedicoERP:
- Electronic sales invoices
- Services provided
- Date of the invoice
- Bill/Cost for services
- PII of customers, such as name, address, and phone number.
- NIT number, essentially a tax identification number used in many Latin American countries.
GPS Trackit
This cloud-based, IoT-enabled platform provides fleet and asset management solutions, including GPS tracking, real-time monitoring, geofencing, route optimization, driver behavior analytics, and video telematics with dashcams.
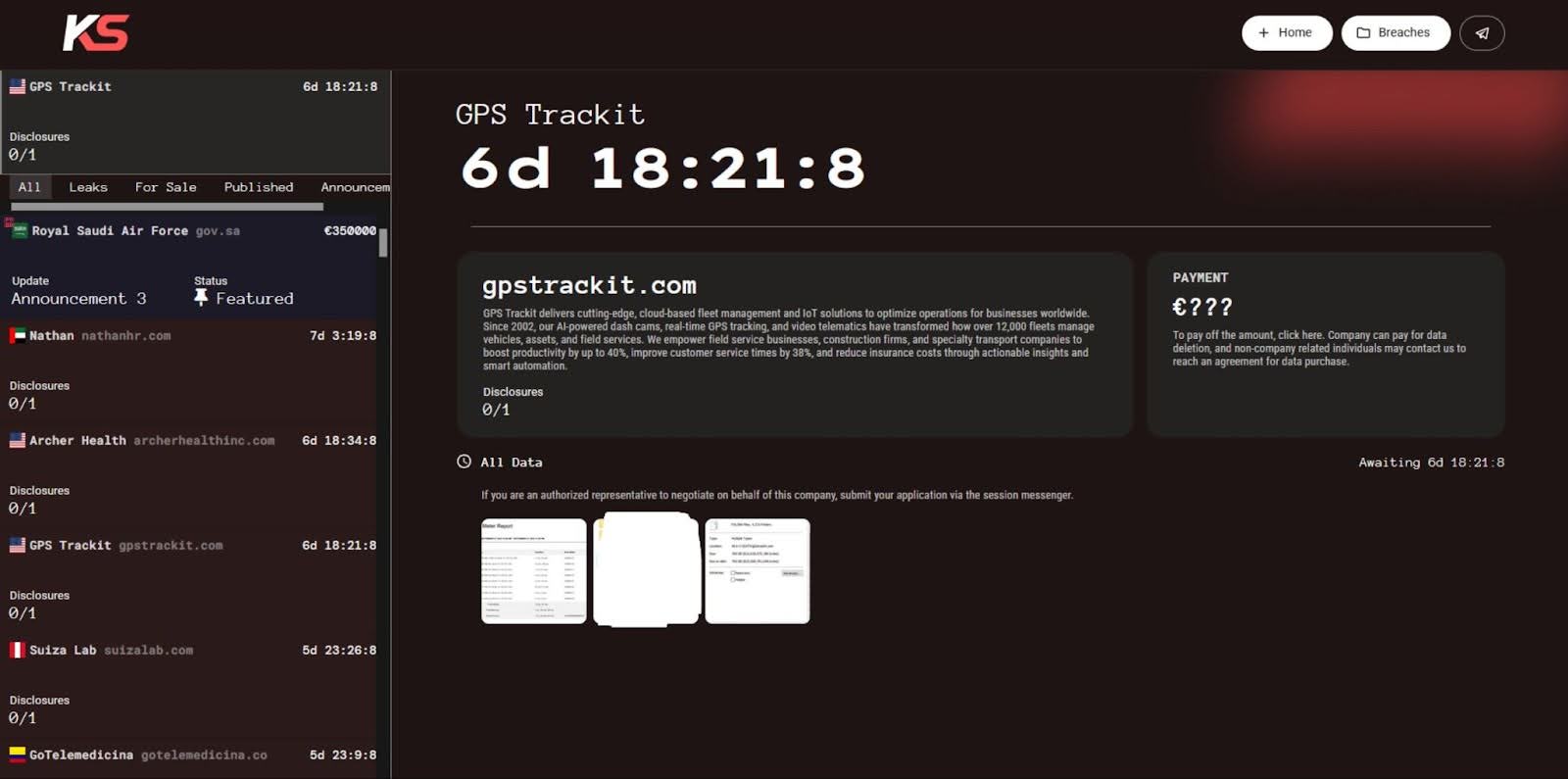
KillSec released 3 screenshots, showing proof of the intrusion and subsequent data exfiltration from a massive dataset. The screenshot reveals the likely access point to be Windows Remote Desktop based on a screenshot showing a Windows directory tree.
The attackers showed a Windows file properties window, showing the size of the data they exfiltrated totals 765 GB, containing 716,986 files across 4,215 folders. This shows extracted reports from highly sensitive telematics data, precise vehicle locations, driver
activities, timestamps, and operational usage metrics.
Ultimately, the data shows live operational intelligence, potentially exposing the company to illegal surveillance, physical theft by exploiting and intercepting fleet movements, and burglaries of parked or unattended vehicles.
GoTelemedicina
GGoTelemedicina is a telemedicine and teleradiology platform out of Colombia, which functions as a centralized service provider for a variety of healthcare institutions for remote diagnostic and consultative services.
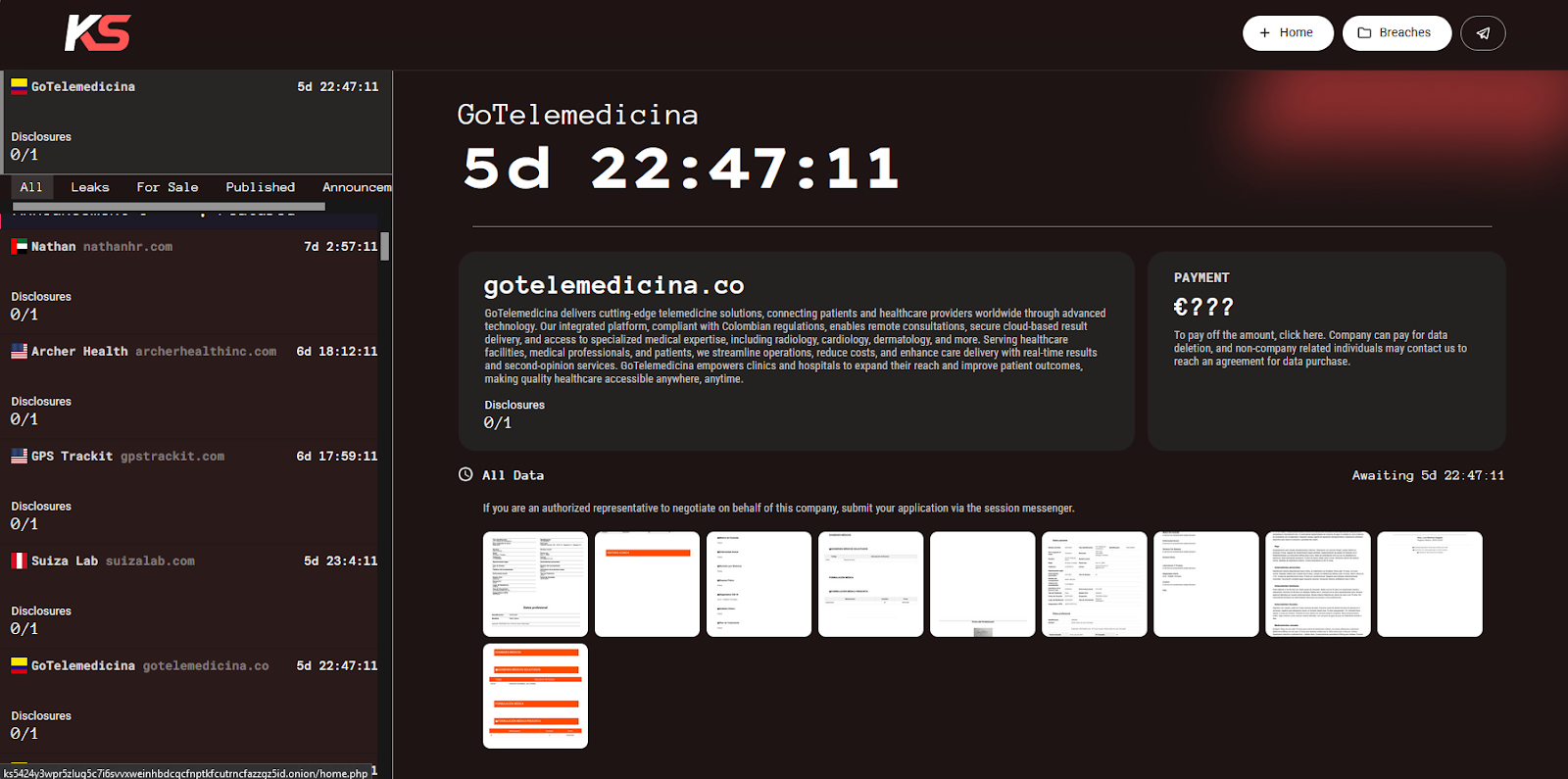
KillSec leaked a batch of 10 screenshots, exposing the following sensitive data:
- Clinical records
- Prescriptions
- Appointment logs
- Medical exam requests
- Detailed patient histories
- Sensitive medical information, such as diagnoses, test orders, and prescriptions
- PII containing full names, national IDs, DOBs, addresses, phone numbers, and emails
- Provider data, such as doctor names, IDs, signatures, and registration numbers.
The extent of the impact these breaches have on clients and patients under targeted healthcare providers is serious, and ransomware gangs are throwing everything they have at these industries.
It should be noted that while the healthcare sector remains among the most targeted industries in ransomware attacks, the current way of diminishing the potential for these attacks to occur isn’t a solution. It only addresses attacks if and when they occur.