Zero-Click Exploit Reveals Location Risks in Signal, Discord

Staying anonymous in the digital world has proven increasingly difficult once again. Our digital footprints can easily be used to track us in the real world. A sophisticated 0-click deanonymization vulnerability has been reported, potentially affecting popular platforms like Signal, Discord, and others. The report, authored by self-taught developer and ethical hacker "hackermondev," highlights a critical privacy risk that has sparked discussions within the cybersecurity community.
Meet the Researcher
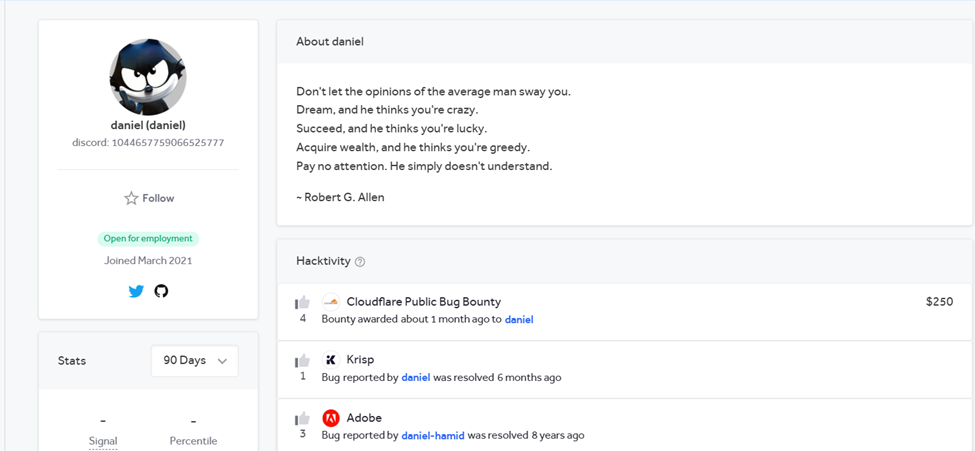
The author and researcher of the report, Hackermondev, who claims his real name is Daniel, describes himself as a curious and driven teenager. He discovered this vulnerability while exploring potential exploits in content delivery networks (CDNs). “I hack billion dollar companies and build cool stuff,” he explains when he talks about himself in the beginning of the report and provided a link to his HackerOne profile. “A few months ago, I had a lightbulb moment: if Cloudflare stores cached data so close to users, could this be exploited for deanonymization attacks on sites we don't control?”
While Daniel claims to be 15 years old, the sophistication of his research and the technical depth of his report have left some in the cybersecurity community skeptical. Given that his X profile opened in November 2017, this claim appears doubtful. Regardless of his age, the findings stand as a testament to a high level of expertise. His work has highlighted a significant privacy gap in how CDNs handle cached resources and should prompt debates about the balance between performance and security in today’s interconnected digital world, especially as location data might be vital for individuals like journalists and dissidents.
We attempted to reach out to Daniel for further comments, but he has not responded at the time of publication.
The Anatomy of the Exploit
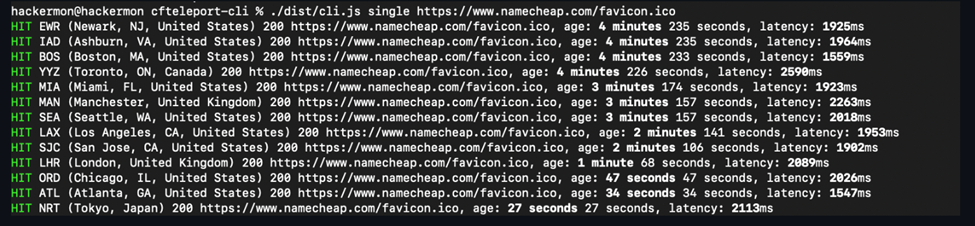
This proof of concept (PoC) attack exploits Cloudflare's caching mechanism and its extensive network of global datacenters to identify a user's approximate location within a 250-mile radius. It uses metadata from HTTP responses, such as cf-ray (which indicates the datacenter handling the request), to infer location data.
-
Cloudflare's Caching Mechanism:
- Cloudflare stores cached resources in local datacenters to improve performance.
- The metadata (cf-cache-status, cf-ray) in HTTP responses reveals the datacenter closest to the user.
-
Cloudflare Teleport Tool:
- A tool developed by the author, leveraging a bug found by another Cloudflare community member in Cloudflare's network to direct HTTP requests to specific datacenters.
- The bug was later patched, but similar attacks were recreated using VPNs to traverse datacenters.
-
Application-Specific Exploits:
- Signal: Attachments cached by Cloudflare can reveal a recipient's location when downloaded automatically via push notifications.
- Discord: Avatar URLs cached by Cloudflare can be used to deanonymize users through friend request notifications.
-
1-Click and 0-Click Exploits:
- 1-Click: Requires the target to interact with a resource, like opening a message or attachment.
- 0-Click: Exploits automatic downloads triggered by push notifications, requiring no user interaction.
Real-World Applications
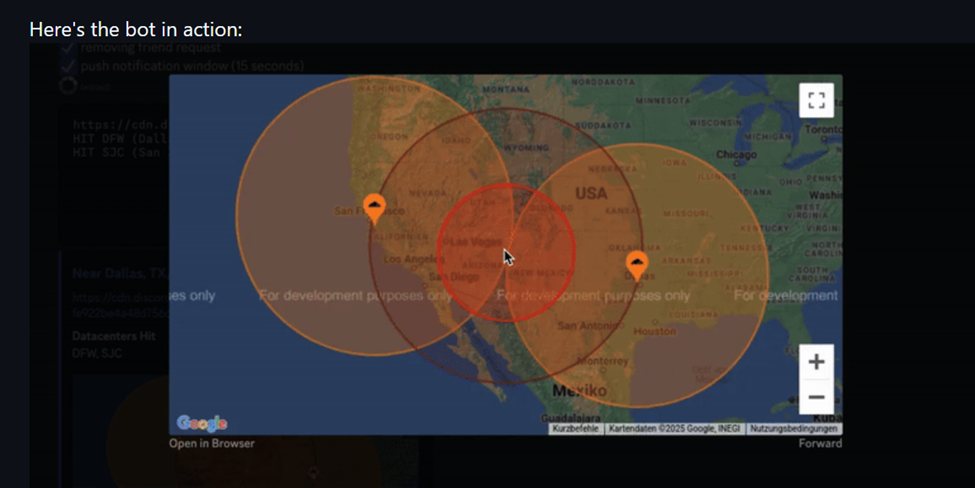
- Signal: Attachments cached on Cloudflare are automatically downloaded during push notifications, enabling location tracking.
- Discord: Custom emojis or avatars, loaded through notifications, allow similar tracking.
- General: The attack can track users of any service utilizing Cloudflare caching.
Targets and Implications
This exploit will affect platforms prioritizing privacy, like Signal, but it could extend to other mainstream services like Discord and others. Given the prevalence of these platforms, the attack has far-reaching implications:
- Whistleblowers and Activists: The attack could expose identities of individuals relying on these platforms for secure communication.
- Everyday Users: Regular users sharing sensitive personal or business information may become unintended targets.
- Enterprise Security: Businesses utilizing these platforms for collaboration may face espionage risks.
Mitigation and Recommendations
Hackermondev informed all Signal, Discord, and Cloudflare about the attack, which he got varying responses. While CloudFlare has patched the related vulnerabilities, the author found a way around that too. Others claimed that it is the users’ responsibility to mitigate risks by themselves.
Protection Measures
-
For Developers:
- Disable caching for sensitive resources.
- Use protocols or services that do not rely on CDNs for critical data.
-
For Users:
- Minimize reliance on apps that use CDNs for sensitive data.
- Stay informed about app updates and security practices.
Users and organizations are advised to adopt the following measures to further minimize risks:
- Update Applications: Ensure all platforms and devices are running the latest software versions.
- Minimize Metadata Leakage: Use features like disappearing messages and avoid sharing sensitive information without additional encryption layers.
- Employ Network-Level Protections: Use tools like VPNs to obscure metadata and limit traffic analysis opportunities.
- Enable Multi-Factor Authentication (MFA): While unrelated to this specific attack, MFA ensures added security for accounts.
The 0-click deanonymization attack illustrates a reminder that even platforms designed with privacy in mind are not immune to exploitation. Hackermondev’s research highlights how vulnerabilities in infrastructure like CDNs can have widespread implications for user privacy. Thanks to his efforts, the cybersecurity community is better equipped to face these challenges head-on.