How Did Telegram Become a Hotbed for Global DDoS Attacks

In August 2024, the arrest of Telegram CEO Pavel Durov by French authorities sparked a wave of Distributed Denial of Service (DDoS) attacks. Hacktivist groups, primarily pro-Russian and pro-Palestinian collectives, targeted French organizations in a campaign tagged #FreeDurov. This episode highlighted the deep integration of Telegram into cybercriminal operations and showed the platform’s central role in organizing DDoS attacks across geopolitical fault lines.
Telegram’s Role in the DDoS Ecosystem

Durov’s arrest resonated within Telegram’s hacktivist communities for two primary reasons. First, many groups viewed the incident as a political maneuver against a platform enabling free speech and anonymous coordination. Second, as Telegram hosts the majority of its operations, any perceived threat to its integrity spurs immediate action. These groups retaliated against France to defend their operational hub and, in some cases, to support Durov ideologically, as some see him as a symbol of resistance to Western authority.
But why Telegram? Why not rely on the dark web, a more traditional space for cybercriminals? The answer lies in Telegram’s accessibility and features. Telegram combines ease of use, end-to-end encryption, and a vast user base, providing threat actors with an ideal blend of anonymity and outreach. Unlike the dark web, which requires specialized tools and knowledge to access, Telegram is user-friendly and publicly accessible.
Furthermore, the dark web has become a heavily monitored space for cybercriminals. Security forces worldwide have ramped up their efforts to dismantle dark web marketplaces and forums, often resulting in high-profile takedowns like those of AlphaBay and Hansa. These operations not only seize platforms but also expose user data, increasing the risk for cybercriminals operating in such spaces. The heavy surveillance and infiltration of dark web forums by law enforcement have made them less appealing for coordination and recruitment. Telegram, on the other hand, offers encrypted channels that allow threat actors to coordinate with minimal risk of detection, while its broad reach enables them to recruit participants and disseminate tools efficiently.
Understanding DDoS Attacks
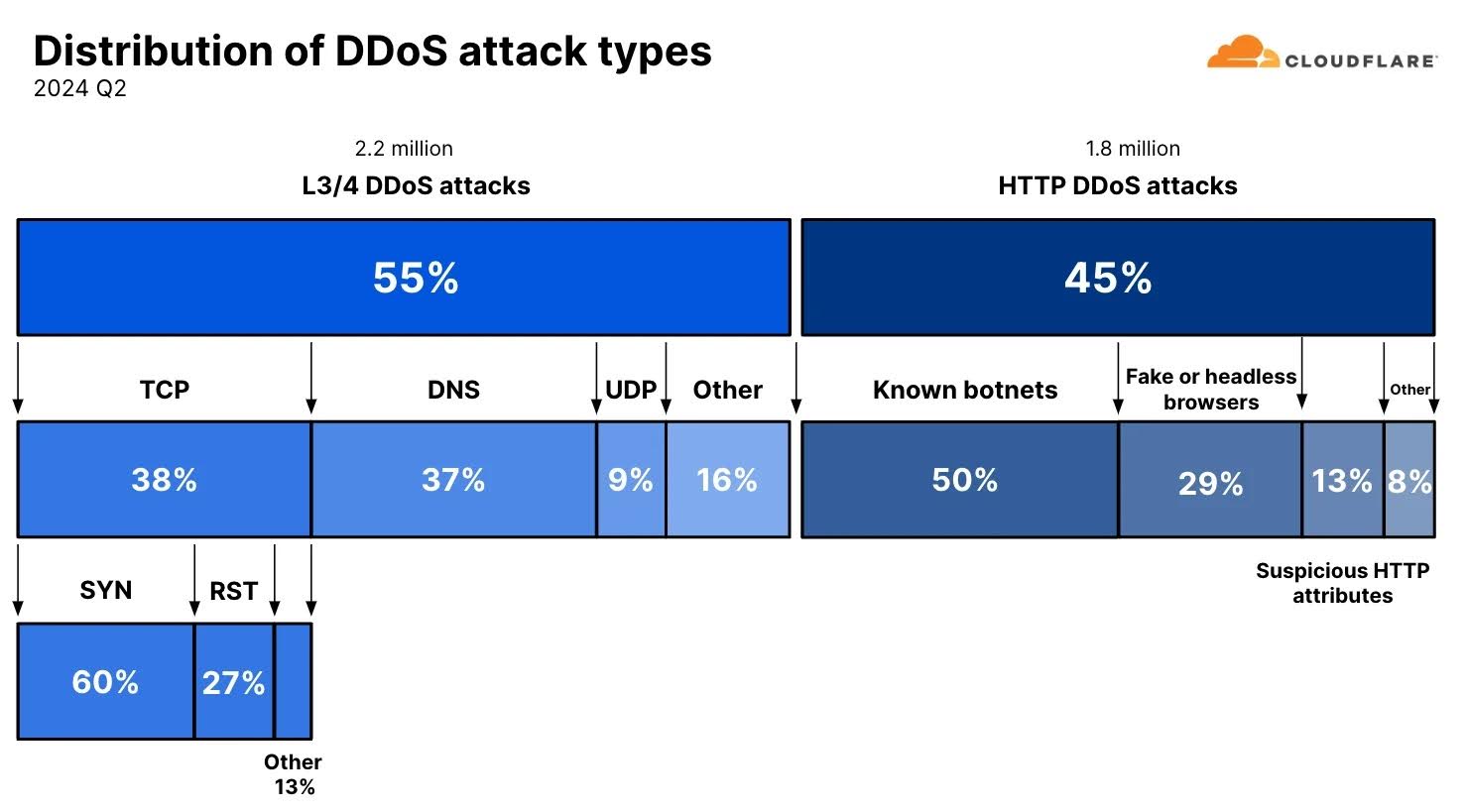
DDoS attacks aim to overwhelm a target’s online services with massive amounts of traffic, rendering them inaccessible. These attacks can disrupt critical infrastructure, financial institutions, and government services. Recent reports indicate that DDoS attacks are becoming increasingly sophisticated, leveraging techniques like multi-vector attacks and crowdsourced botnets to maximize impact. The ease with which these tools can be distributed via Telegram has amplified the threat, making it accessible to even novice cybercriminals.
A Growing Trend: DDoS-as-a-Service
Beyond hacktivist campaigns, Telegram has also become a marketplace for DDoS-as-a-Service (DDoSaaS). Vendors openly advertise booters and stressors—tools enabling clients to rent botnets for targeted attacks. These services are often marketed on Telegram with detailed pricing structures, ranging from as low as $10 for basic attacks to thousands of dollars for sophisticated, high-intensity campaigns. For example, according to FalconFeeds.io’s reporting on DDoS attacks, tools like Lava C2/API and Solar Services provide advanced features such as Layer 4 & Layer 7 attack methods and capabilities to bypass common defenses like Cloudflare. This commoditization of DDoS tools has lowered the barrier to entry, making these attacks accessible to anyone willing to pay.
The Traits of Telegram-Based Threat Actors
As of the end of 2024, most groups orchestrating DDoS campaigns on Telegram can be classified into three broad categories. These classifications are not static, and the landscape will likely evolve over time:
1. Pro-Russian Hacktivists
These groups align with Russia’s geopolitical interests, targeting NATO countries and Ukraine’s allies. Their methods include advanced DDoS tools, cryptocurrency rewards for participants, and propaganda to rally support. Below are some notable groups:
- NoName057(16): NoName057(16) is one of the most sophisticated pro-Russian hacktivist groups. They operate the DDoSia Project, a platform that gamifies DDoS campaigns by incentivizing volunteers with cryptocurrency rewards. Their primary targets include Ukrainian government websites, NATO member states, and Western financial institutions. The group’s methods are characterized by encrypted tools, such as AES-GCM, to protect target lists and obscure attack details. In late 2024, NoName057(16) expanded its operations to target Scandinavian banks and government websites, further illustrating its adaptability. Their coordination with other pro-Russian and Islamist hacktivists has strengthened their reach and operational impact.
- UserSec: Known for DDoS-for-hire services and politically motivated campaigns, UserSec’s activities include attacks on critical infrastructure and data breaches. They collaborate with other pro-Russian hacktivist groups to execute large-scale attacks.
- Cyber Army of Russia Reborn (CARR): A significant player in the #FreeDurov campaign, CARR targets Ukrainian and NATO assets. The group has also been linked to attacks on SCADA systems in critical infrastructure across Europe and the U.S.
- CyberDragon: Active since 2023, this group focuses on NATO and Ukrainian targets, often in coordination with other pro-Russian entities. Their participation in campaigns like #FreeDurov shows their role as a reliable ally in Russia-aligned hacktivism.
2. Pro-Palestinian Hacktivists
These groups focus on targeting Israeli entities and their allies. They utilize crowdsourced tools and campaigns to disrupt critical services and draw attention to their causes. While no explicitly pro-Israeli groups have been identified, pro-Israeli efforts may counterbalance these campaigns, especially during heightened geopolitical tensions. Examples of pro-Palestinian groups include:
- RipperSec: RipperSec is a Malaysia-based pro-Palestinian hacktivist group renowned for developing the MegaMedusa tool, a Layer 7 DDoS platform. MegaMedusa simplifies the process of launching high-impact attacks, making it accessible to even inexperienced operators. During the #FreeDurov campaign, RipperSec targeted French financial and governmental institutions. Their primary focus, however, remains on Israeli assets, including financial institutions and media outlets. RipperSec’s collaboration with pro-Russian groups like NoName057(16) amplifies their reach and highlights their adaptability in leveraging global alliances for localized goals.
- Cyber Army of Palestine: This group coordinates crowdsourced DDoS campaigns, such as “Toffan,” targeting Israeli news outlets, financial institutions, and government agencies. The group’s campaigns are ideologically driven, with participation incentivized by leaderboards and rewards linked to Hamas figures.
- Dark Storm Team: Known for selling DDoS tools alongside conducting attacks, this group collaborates with both pro-Palestinian and pro-Russian entities. Their methods include targeted attacks on Israeli websites and occasional campaigns against unrelated entities for financial gain.
- Golden Falcon: This group frequently aligns with other pro-Palestinian actors to execute DDoS attacks and website defacements, particularly targeting Israeli government and defense sectors.
- MR. Hamza: A smaller but significant player in pro-Palestinian hacktivism, MR. Hamza specializes in exploiting vulnerabilities in under-protected sites. The group uses Telegram channels to distribute simplified attack tools, making their campaigns accessible to less skilled operatives. Their targets often include smaller Israeli businesses and public sector entities.
3. Others
- IT Army of Ukraine: This pro-Ukrainian group leverages crowdsourcing to disrupt Russian digital assets. Operating primarily through Telegram, the IT Army of Ukraine disseminates target lists and DDoS tools to volunteers, enabling large-scale coordinated attacks against Russian government websites and businesses. Their activities are a direct response to the ongoing Russia-Ukraine conflict and serve as a countermeasure to pro-Russian hacktivists.
- GlorySec: Identifying as an anti-authoritarian group, GlorySec targets governments perceived as corrupt, including Russia and China. They employ DDoS attacks, data breaches, and website defacements, occasionally aligning with other hacktivist groups for larger campaigns.
- Anonymous Guys: Based in Iran, this group focuses on ideological campaigns defending Islamic values. Their attacks frequently target Israeli and Western entities. Despite their independence, they collaborate with pro-Russian hacktivists to bolster their efforts.
Conclusion
Telegram’s rise as a hub for organizing DDoS attacks highlights the evolving nature of the cyber threat landscape. While initially perceived as a secure messaging platform, Telegram has become a battleground where hacktivist groups and cybercriminals exploit its features to coordinate large-scale operations. As geopolitical tensions escalate, the role of platforms like Telegram in enabling such activities demands greater scrutiny. Addressing this challenge requires a combination of proactive monitoring, robust cybersecurity measures, and international collaboration to curb the misuse of widely accessible technologies.