How Top 51 Crypto Apps Are Putting You in Danger

The devil is in the details, and so is the security of top cryptoasset apps. Hundreds of millions of people are using crypto apps to invest, trade, pay for goods, buy NFTs, or for other purposes, yet too often they overlook the significant security and privacy risks that come with them.
Researchers at LEAKD conducted a static analysis of 51 top downloaded crypto apps from Google Play, uncovering alarming security and privacy concerns. One of the most alarming findings is the volume of hardcoded secrets embedded within some of these apps, which poses a serious risk of unauthorized access and data breaches.
It becomes even more important, as governments increasingly seek to regulate the crypto space, requiring you to provide sensitive details like ID verification. While such measures are often justified as necessary for your security, they are not solely driven by security concerns. These regulations also aim to enhance control and oversight over financial activities, raising the stakes for you if these apps are exploited by threat actors.
Alarming Findings
Using static analysis, the LEAKD team dug deep into how 51 of the most downloaded crypto apps on Google Play manage permissions, network configurations, embedded trackers, and hardcoded secrets. What we have found is both surprising and concerning: many apps overreach by requesting unnecessary permissions, show glaring security weaknesses, and fail to adhere to even basic privacy standards, putting you at considerable risk.
These vulnerabilities aren’t just theoretical. Excessive permissions and insecure configurations can lead to:
- Data Theft: Sensitive user information, including identity documents and private keys, can be intercepted.
- Account Takeovers: Hardcoded secrets and weak authorization controls provide attackers with easy entry points.
- Privacy Breaches: Overuse of trackers undermines user anonymity, exposing personal activity to third parties.
Privacy Risks from Trackers
Trackers silently collect data about how you interact with an app—and sometimes even your activities outside of it. While permissions dictate what an app can access, trackers often go unnoticed, harvesting information that can paint an intimate picture of your behavior, habits, and preferences. The pervasive presence of trackers poses a significant threat to privacy, as they often share sensitive data with third-party entities, exposing you to targeted advertising, profiling, and potential misuse of their personal information.
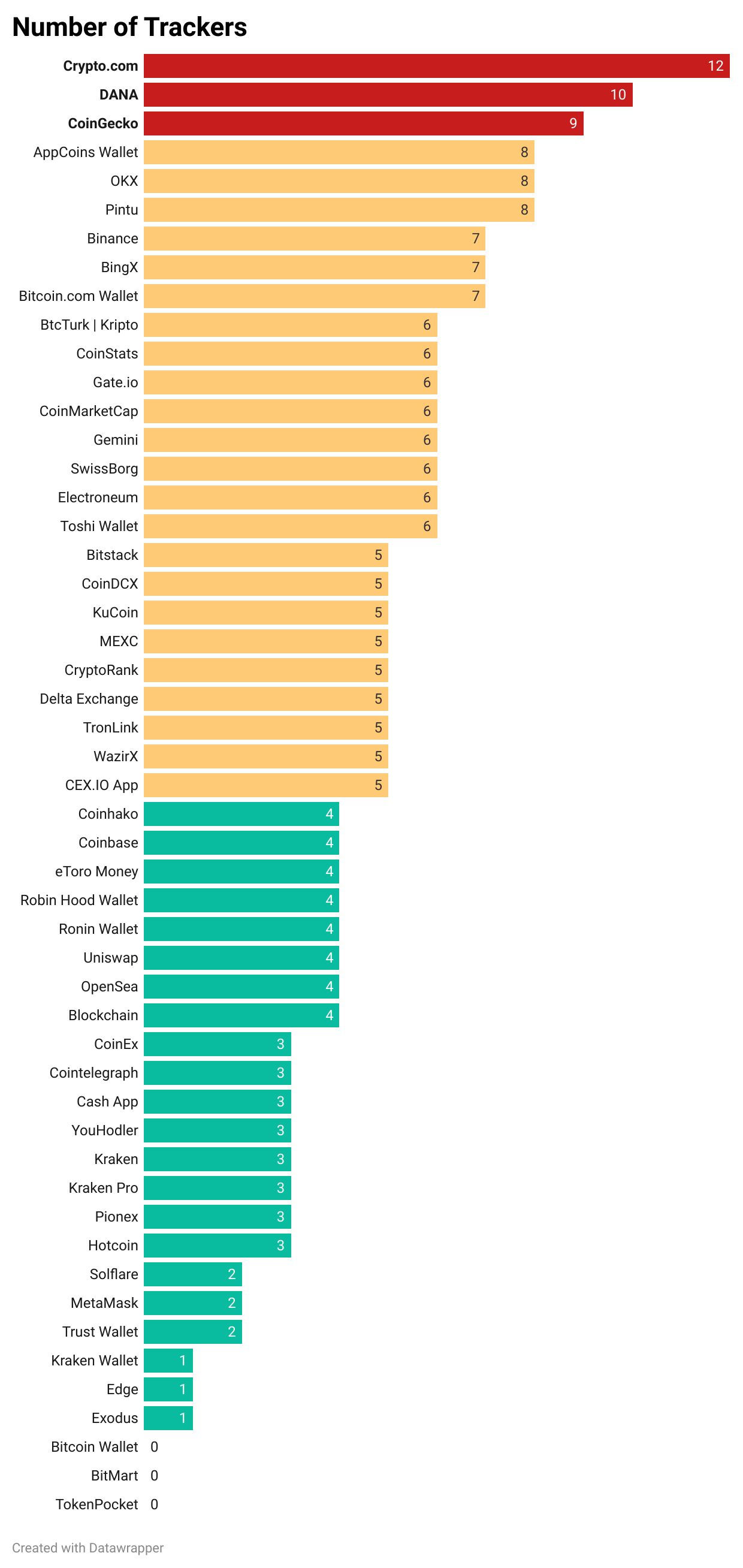
The apps like Crypto.com and DANA had over 10 trackers each, enabling extensive data collection and potentially compromising your anonymity while the average was 4.6. These trackers often collect behavioral data, including browsing habits, device information, and even location, which can then be shared with third parties or used for targeted advertising. While some trackers are used to improve user experience or provide analytics, the sheer number and lack of transparency regarding their use raise red flags. Interestingly, some apps demonstrate that fewer trackers are sufficient for functionality. Bitcoin Wallet, TokenPocket, and BitMart had zero trackers, showcasing that it is possible to maintain app functionality without excessive data collection.
Remember - you should be wary of apps with excessive trackers and demand greater transparency from developers about how this data is used and shared. Developers, in turn, must limit tracker usage and ensure that their inclusion is both essential and transparent, reflecting the core values of the crypto community.
Hardcoded Secrets: Hidden Risks in Crypto Apps
While trackers quietly collect data in the background, hardcoded secrets present a more overt and critical threat to your security. These embedded secrets—including API keys, authentication tokens, and sensitive system configurations—are directly baked into the app's code. If exposed, they provide attackers with a straightforward route to compromise critical systems, gain unauthorized access, or manipulate app functionalities. The analysis highlights the staggering variation in the presence of such secrets, warranting scrutiny of app development practices.
Many of the apps analyzed by LEAKD researchers were found to contain hardcoded secrets embedded within the code. While some level of hardcoding may be necessary for legitimate reasons, such as enabling specific app functionalities, these practices introduce significant security risks. Hardcoded secrets can be inadvertently exposed during app decompilation or reverse engineering, providing attackers with direct access to backend systems, APIs, or user accounts.
The analysis uncovered a striking variation in the number of hardcoded secrets across apps. While some apps like Kraken Wallet and MetaMask had fewer than 15 hardcoded secrets, others exhibited alarmingly high numbers. OKX stood out with 5,329 secrets, Binance with 1,937, and MEXC with 1,340. Although such counts could partly reflect false positives in the Mobile Security Framework (MOBSF) analysis, the sheer scale of these numbers raises questions about their necessity and the potential for misuse.
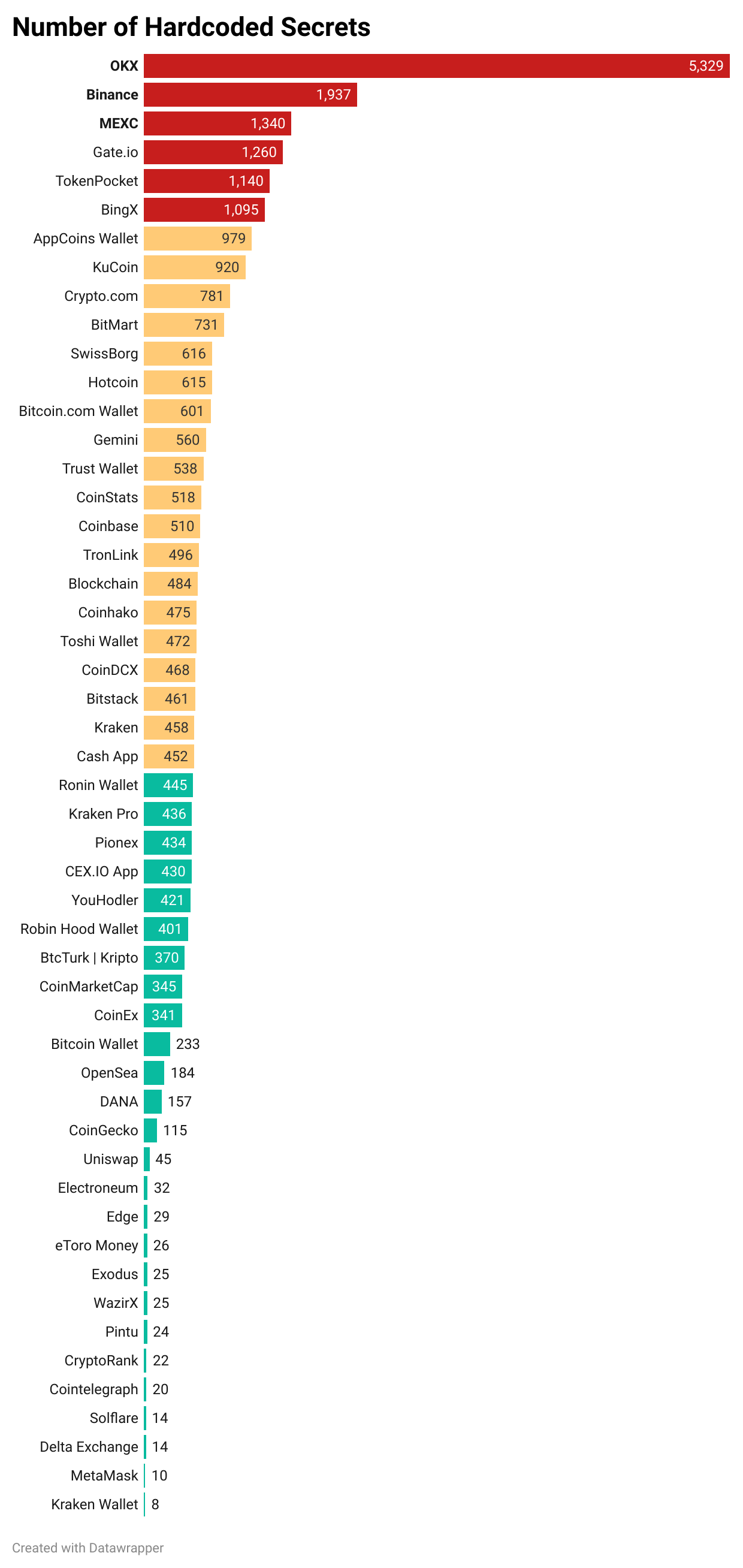
The high number of secrets in certain apps suggests either poor secret management practices or an over-reliance on hardcoding sensitive data, both of which increase the risk of unauthorized access or data breaches. To mitigate these risks, developers must assess the necessity of embedding sensitive data within their apps and implement robust mechanisms to secure them. You, on the other hand, should be cautious of apps with unusually high numbers of hardcoded secrets and demand greater transparency from developers about how their data is being protected.
Excessive and Irrelevant Permissions
One of the most disturbing issues identified in the study was the sheer number of permissions requested by the apps. On average, each app requested around 22.9 permissions, with some going as high as 45, as seen in apps like Binance. These excessive permissions create a large attack surface, making you more vulnerable to exploitation.
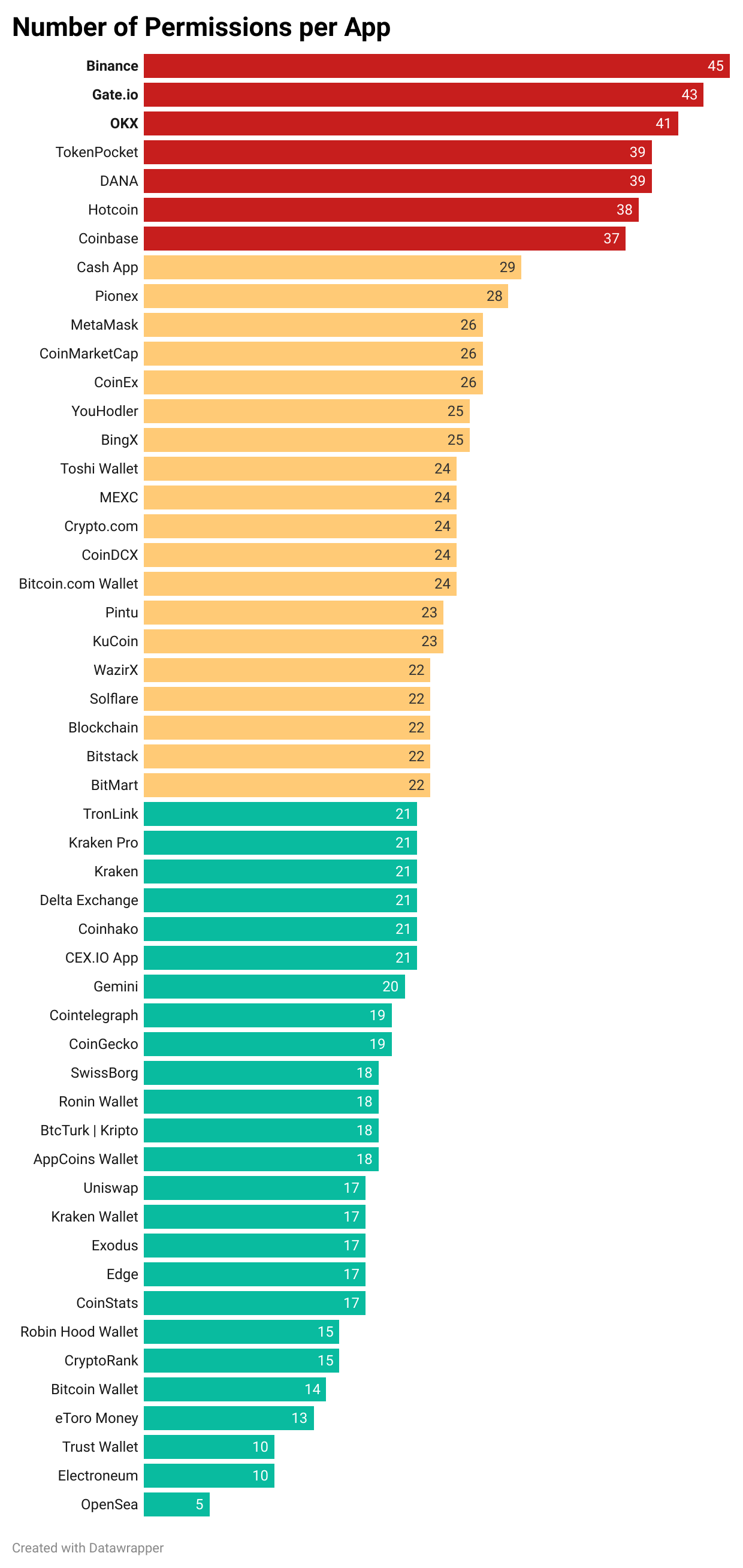
Some permissions, while necessary for certain features or regulatory compliance, still pose significant risks. For example, permissions like CAMERA, READ_EXTERNAL_STORAGE, and WRITE_EXTERNAL_STORAGE are often required for identity verification processes mandated by governments. CAMERA is used to capture images of identification documents, while READ_EXTERNAL_STORAGE and WRITE_EXTERNAL_STORAGE allow apps to access and save these documents on your device. However, mishandling these permissions can lead to unauthorized access or breaches, exposing sensitive user information. These permissions allow apps to capture and store sensitive documents but, if mishandled, can lead to unauthorized data leaks or breaches.
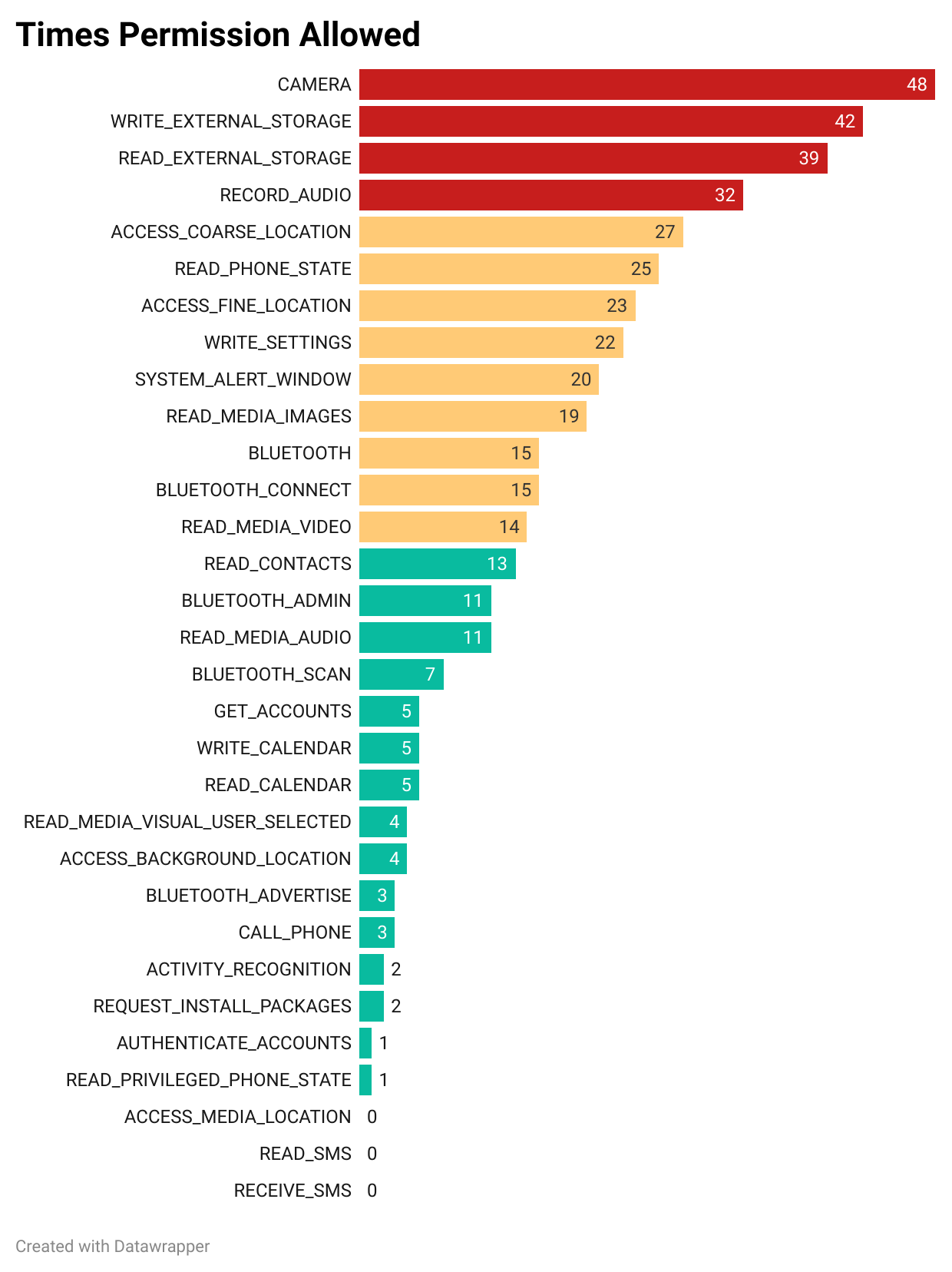
There are some other permissions that also raise concerns. For instance, RECORD_AUDIO can be exploited to eavesdrop on you, while ACCESS_FINE_LOCATION and ACCESS_COARSE_LOCATION enable precise or approximate location tracking, potentially exposing sensitive movement patterns. SYSTEM_ALERT_WINDOW is another dangerous permission, often used by malicious actors to create phishing overlays that trick users into sharing sensitive data. Lastly, READ_PHONE_STATE allows access to critical device information, such as your phone number and network details, which could be exploited for attacks or identity theft. These permissions allow apps to capture and store sensitive documents but, if mishandled, can lead to unauthorized data leaks or breaches.
However, the study also identified permissions that appear to be completely irrelevant to crypto app functionality. Examples include WRITE_CALENDAR, BLUETOOTH_ADMIN, and ACTIVITY_RECOGNITION. These permissions highlight a troubling trend of over-permissioning, which not only compromises your privacy but might also erode trust in these applications.
Recommendations for Users
Here’s how you can protect yourself:
- Be Permission-Conscious: Before installing an app, check the permissions it requests. Avoid apps asking for irrelevant permissions.
- Opt for Secure Options: Choose apps with a proven track record of security and transparency.
- Use Separate Wallets: Avoid storing large amounts of cryptoassets in apps with questionable security.
Conclusion
These findings by the LEAKD team should serve as a wake-up call for both users and developers in the crypto space. While crypto apps are becoming increasingly more convenient, they often come with hidden risks that can compromise your security and privacy. The staggering number of hardcoded secrets found in some apps highlights the need for greater transparency and better development practices to safeguard sensitive information. By demanding better security practices and making informed choices, you can protect your assets and personal information from potential threats.
Comments