120K Clients at Risk: Mexico-based financial management company Leak

A misconfigured Amazon S3 storage container used by Orderly, a Mexico-based financial management software company, exposed the sensitive data of 120,000 clients.
Orderly offers a streamlined approach to various financial automation management, which simplifies administrative tasks for creative businesses, serving over 350 companies, according to their website.
The platform also offers automated invoicing, enhanced payment collection efficiency, and simplifies financial reporting. This further emphasizes the severity of the data leak when a multi-faceted financial efficiency management service suffers a leak due to inefficiency with S3 storage configurations.
Leaked.com security researchers discovered the unprotected data, emphasizing the severity of cloud-based security misconfigurations, which can occur when companies fail to implement appropriate access controls that protect from intruders looking to commit fraud at the company’s expense.
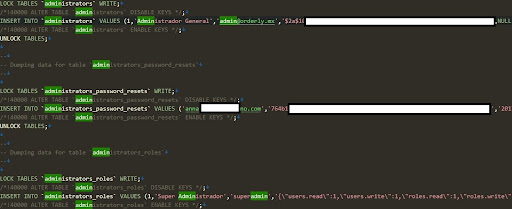
The data exposed includes plaintext admin passwords, financial invoices, tax documents, and other client personal identifiers, which leaves clients completely exposed to identity theft and fraud. The leak also exposed SQL databases, including the server backup and an SQL script used to back up the database structure for schema recreation.
For example, the leak contains 17,269 highly sensitive Microsoft worksheets containing private customer information and financial records. More importantly, because these files are exposed, it could allow threat actors to download the unprotected information, make modifications to the files, and write the changes to the server.
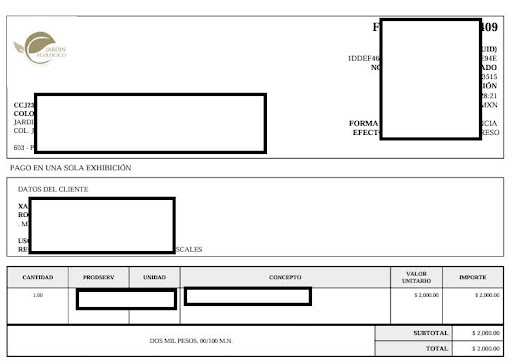
Furthermore, due to exposed credentials stored in plaintext, attackers could make short work of compromising individual customer accounts in the absence of any standard credential encryption.
Hacker’s Persistence through S3 Misconfigurations
An S3 bucket is a cloud storage container, which is a component of Amazon Web Services. This is where you can store files, such as documents, media files, and of course server backups. This also means S3 buckets are ideal for website hosting, etc.
Therefore, if an S3 bucket is misconfigured, anyone on the internet can find, view, and access the sensitive documents. Threat actors can upload, remove, and alter the contents, such as siphoning data, or establishing long-term persistence by uploading malicious code inside an organization’s cloud infrastructure.