20TB Breach: INC Ransom Steals Genomic Data & Software From Singular

The double-extortion ransomware gang INC Ransom claims to have compromised Singular Genomics, a California-based biotechnology company, in a multi-server attack. The attackers claim to have siphoned 20 TB of files, encompassing a broad range of data, with conspiratorial overtones.
INC Ransom’s public leak site on Tor framed the breach as an attack on Deerfield Management Company, a New York–based investment firm specializing in healthcare and biotechnology, by highlighting one of its portfolio companies, Singular Genomics.
The ransom group accurately described the firm as one of the largest dedicated healthcare investment firms in the world. This sets the tone of the attack by emphasizing its global impact, which embellishes INC Ransom’s own role in a “larger-than-life” cyberattack.
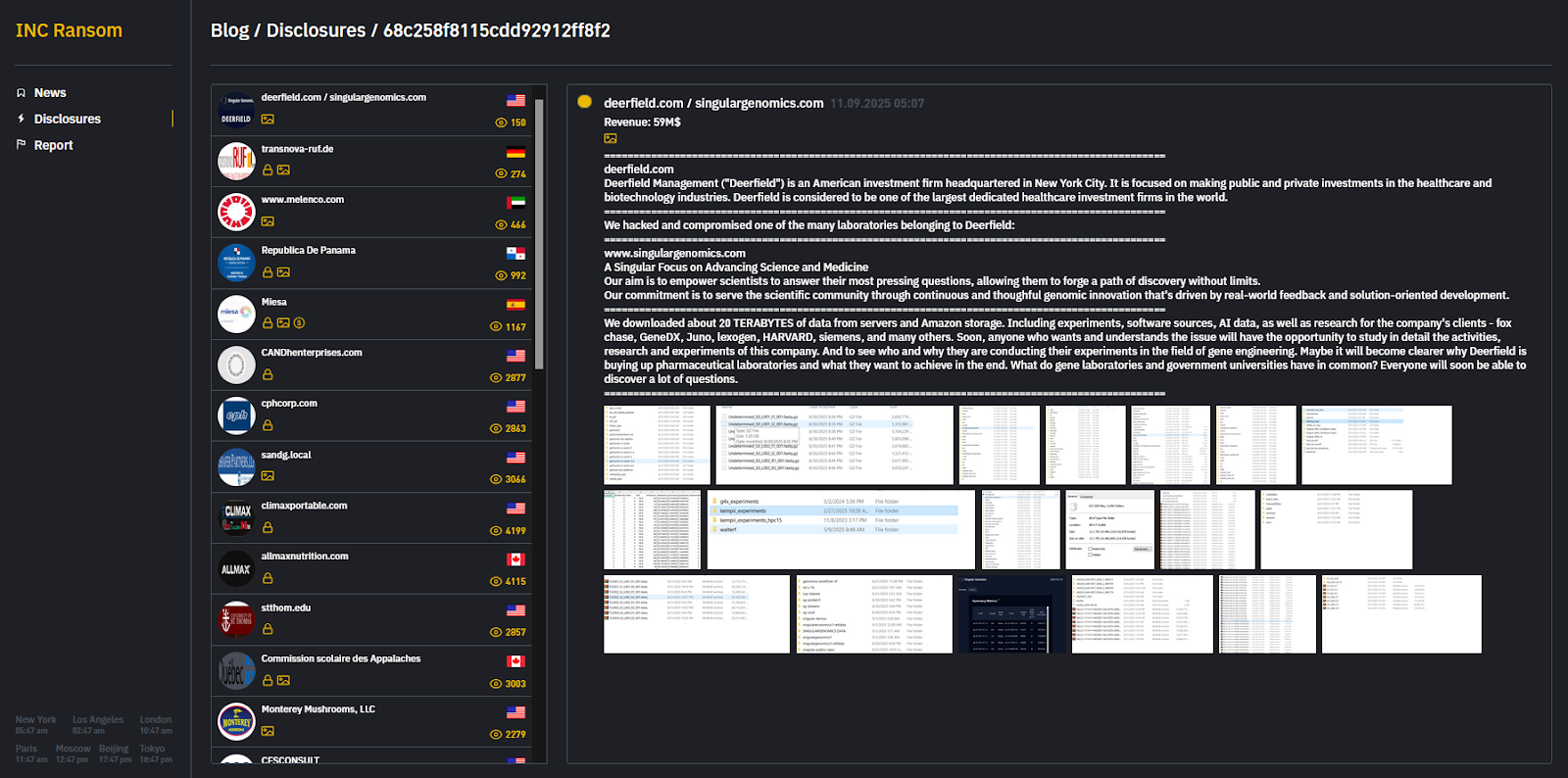
“We hacked and compromised one of the many laboratories belonging to Deerfield,” the group claimed, offering 19 screenshots as proof of the intrusion and subsequent data theft, along with a rather generous insight into Deerfield’s working relationship with Singular Genomics:“We downloaded about 20 TERABYTES of data from servers and Amazon storage. Including experiments, software sources, AI data, as well as research for the company's clients - fox chase, GeneDX, Juno, lexogen, HARVARD, siemens, and many others. Soon, anyone who wants and understands the issue will have the opportunity to study in detail the activities, research and experiments of this company. And to see who and why they are conducting their experiments in the field of gene engineering. Maybe it will become clearer why Deerfield is buying up pharmaceutical laboratories and what they want to achieve in the end. What do gene laboratories and government universities have in common? Everyone will soon be able to discover a lot of questions.”
What the Images Reveal
INC Ransom’s batch of screenshots, essentially serving as “proof-of-hack” material, show internal file directory listings along with Amazon S3 cloud storage dashboards that feature an AWS-like user interface. This suggests the group successfully breached cloud storage systems, supporting their claim of downloading “20 TB of data from servers and Amazon storage.”
The evidence implies that the attackers either obtained valid credentials and accessed the Singular Genomics servers by compromising a remote desktop endpoint. From there, attackers can perform lateral movement across networks and into cloud environments. However they gained access, it's likely the machine they accessed had AWS credentials, cached tokens, or mapped cloud drives.
Many of the files in the screenshots contain raw DNA sequencing reads, which strongly suggests INC Ransom accessed genomic pipelines, and not only the common run-of-the-mill administrative files most ransomware groups search for.
The screenshots also reveal that the attackers stole proprietary analysis software and scripts. With sequencing data in their possession, they could even de-anonymize genomic information and trace it back to individuals by cross-referencing public datasets.
Ultimately, this constitutes wholesale intellectual property theft, particularly in regard to the stolen proprietary software and source code. By comparison, the compromise of human resources, partner, and client data almost pales in significance next to the scale of this scientific data theft.