Cybercriminals Leak Sensitive Data from Elmcrest Kids’ Center

Yesterday, the ransomware gang known as Interlock breached Elmcrest Children’s Center, a nonprofit organization headquartered in Syracuse, New York, that provides care and support to at-risk children and families. The group leaked sensitive data.
The data leak was published on Interlock’s leak site on the Tor network, presented as a parent directory tree, totaling 448.24 GB of exfiltrated data, with folders that appear to be associated with internal facilities or administrative network shares.
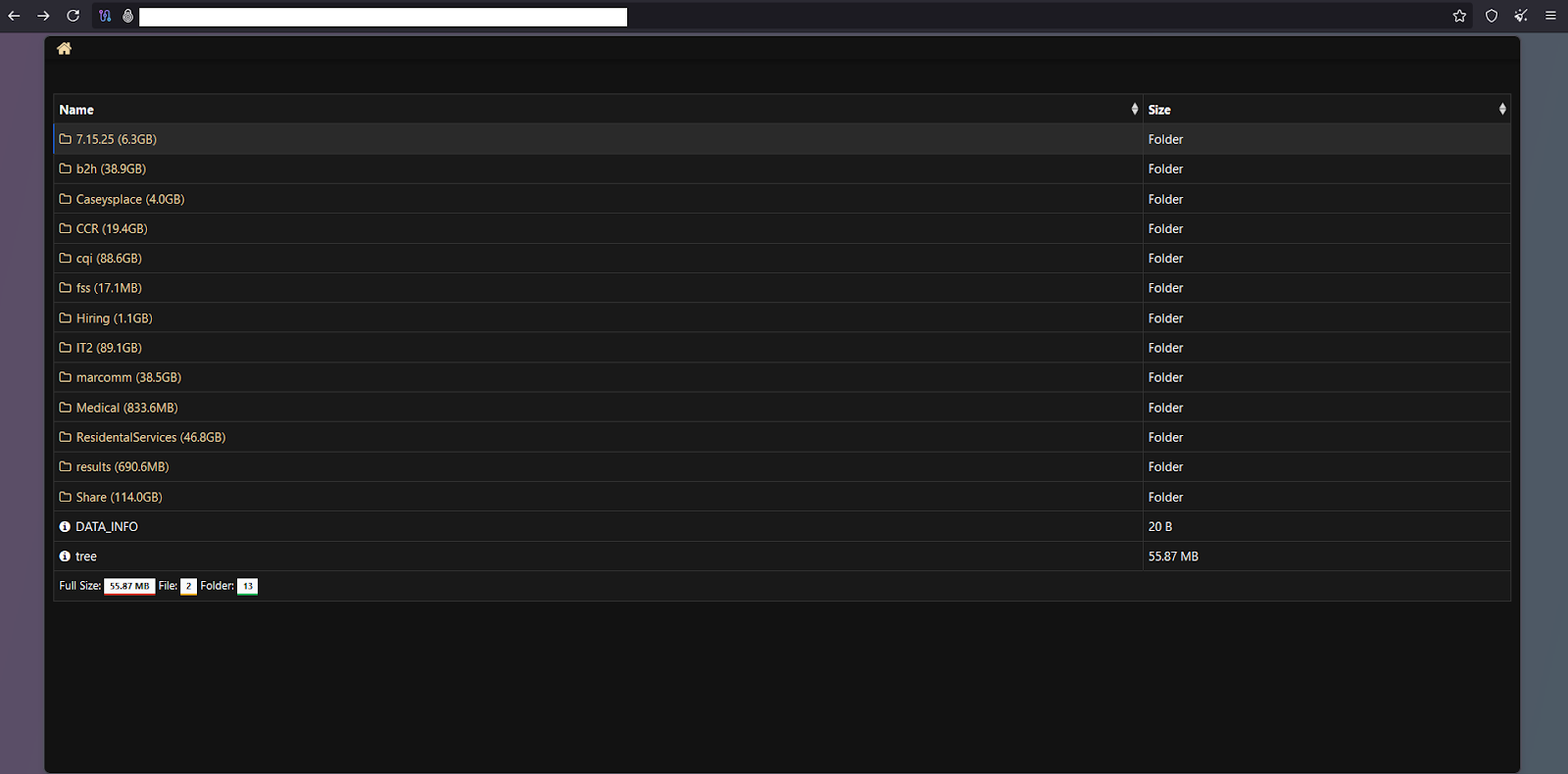
Ultimately, the leak contains extremely sensitive personal identifying information and HIPAA-protected health records, such as the full names of children, birthdates, and care management and treatment plans.
Furthermore, client incident reports, which also contain extremely sensitive details about underage patients, such as suicide attempts of children, incidents surrounding runaways, criminal infractions, and even a record detailing a death by suicide incident by a child. These records include the names of parents, addresses, phone numbers, Medicaid Client ID numbers, and descriptions of the incidents.
Leaked researchers reached out to a hacktivist group calling themselves APT5201 for comment on understanding what hacktivists, especially those who labor in online child protection initiatives, think of attacks of this nature that target the vulnerable.
“This is becoming a war these [explicitive] have invited to their doorsteps,” said their spokesperson. “They want to attack programs helping kids? Okay. Go ahead. Consequences are coming. They could have censored those parts of the records but clearly don’t give a [explicitive]. So yeah, consequences are coming.”
Who is Interlock
The ransomware group Interlock first surfaced on the threat map in late September 2024, and has since made organizations across North America and Europe its central attack surface. The group frequently attacks sectors such as healthcare, government, education, and critical infrastructure.
The group operates under a Ransomware-as-a-Service (RaaS) model and employs sophisticated means to compromise its targets. Such as the following attack vectors:
- Drive-by-downloads. These occur when malicious software is automatically downloaded onto a victim’s device by simply visiting a compromised or malicious website.
- Social engineering. The group uses social engineering toolkits like ClickFix and FileFix, which trick users into copying malicious PowerShell commands using fake CAPTCHAs or folders.
- Remote Access Trojans. The group operates its own Interlock RAT, which can execute PowerShell scripts, keyloggers, and other credential-stealing tools.
- Then, the group uses lateral movement and privilege escalation methods using AnyDesk, PuTTY, and Cobalt Strike, as well as stolen credentials to pivot across networks in search of sensitive files.
- They use tools like AzCopy and Azure Storage Explorer to exfiltrate sensitive information to cloud storage accounts under their control. Once the data is secured in their possession, they execute their encryption payload. Usually, ransomware encryptors append .interlock or 1nt3rlock extensions.
Interlock describes their community as “a relentless collective that exposes the recklessness of companies failing to protect their most critical assets. … We exploit the vulnerabilities they leave wide open, delivering a harsh but necessary wake-up call to those who think they can cut corners on security.”
This kind of manipulative framing is always riddled with ethical contradictions that lack common sense, by firstly equating criminal behavior with a form of public service or ethical enforcement.
Furthermore, when groups claim to seek accountability, they rarely include themselves in that equation. Their descriptions of how their operations function are often theatrical fluff, a narrative crafted to mislead readers and camouflage the fact that it's ultimately about stealing money.
The long-winded explanations are merely an attempt to disguise extortion as ethical enforcement. In the end, the justification collapses, especially when it attempts to defend exposing sensitive data on at-risk children to threat actors abroad.