Dark Web Leak: PKO Bank Polski Employee & Device Records Exposed

A member of the notorious cybercrime forum DarkForums allegedly leaked a dataset containing sensitive information belonging to employees of PKO Bank Polski, Poland's largest financial institution. The dataset appears to have been listed for sale on the dark web, raising concerns about potential exploitation.
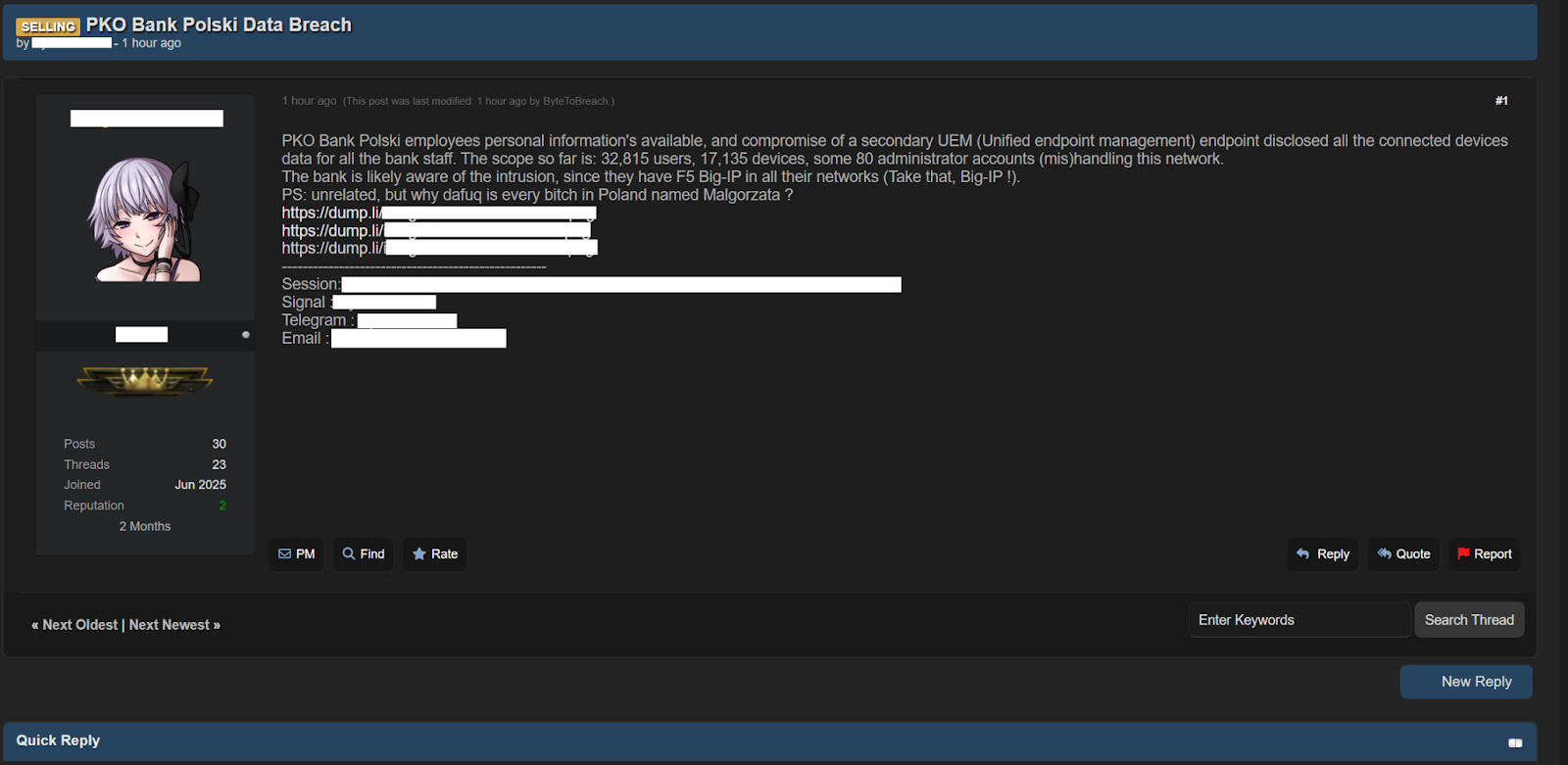
According to the forum post, the information obtained by the threat actor goes beyond general employee records, claiming that a compromised UEM (Unified Endpoint Management) endpoint exposed data tied to every connected device used by staff.
This means the breach contains a rich amount of data that would provide invaluable insights into the bank’s internal device management infrastructure. In turn, this could potentially open opportunities for further attacks.
Furthermore, the post adds the following description of the data breach:
- 32,815 user accounts
- 17,135 registered devices
- Roughly 80 administrator-level accounts were allegedly mishandling network controls.
The post also states:
The bank is likely aware of the intrusion, since they have F5 Big-IP in all their networks (Take that, Big-IP!).
For clarification, F5 Big-IP is an application delivery controller and load balancer widely deployed in enterprise and banking environments. In this context, it is part of the bank’s infrastructure defense, despite the taunt implying the actor managed to bypass or exploit it.
Additionally, the post contains off-site links to screenshots that appear to show the exfiltrated data for sale on an unidentified dark web marketplace, which has not been ascertained. An analysis of the screenshots contains data in stored XML format, as well as what could be a raw SQL dump exported into a CSV or JSON file.
The Data Breach Contents
We analyzed the information in the screenshots, which shows the following:
- Unique device identifiers/fingerprints
- Hardware serial numbers
- Device MAC addresses of network and mobile devices
- Internal asset management tags
- Device names
- Usernames
- Email Addresses
- Location Group Names (from organizational grouping)
- Platform/Operating system used
- Device models
- Last seen time stamps
- Personally identifying information (PII)
The PII in the screenshot consists of a static list of employee email addresses under the PKO Bank domain, formatted as first name plus last name. Because these email addresses are unique identifiers tied to specific bank employees, they qualify as PII under GDPR and other privacy regulations.
Post-Intrusion Expectations
What is interesting about this dataset is that it's unusual, simply because it combines employee PII with device management data. In simple terms, the data connects employees to the devices they use on the network. This is a potential avenue for device spoofing, phishing campaigns, and privilege escalation inside the bank’s network.
There is also the risk of privilege escalation through administrator accounts, since the post highlighted about 80 administrator-level users. Compromising even one of these could allow an attacker to create malicious profiles, wipe devices, or install malware across the entire network. It is important to note that the current breach appears to expose employee accounts and device records, but not the contents of those accounts.
Ultimately, the attack vectors available from this standpoint are virtually endless.