Dark Web Vendor Claims Breach of Anuvu: AWS & Employee Data

Anuvu (Global Eagle), a U.S.-based provider of high-speed satellite connectivity and entertainment for airborne and naval markets, has allegedly fallen victim to a cyberattack by an unknown threat actor who posted evidence of the intrusion online.
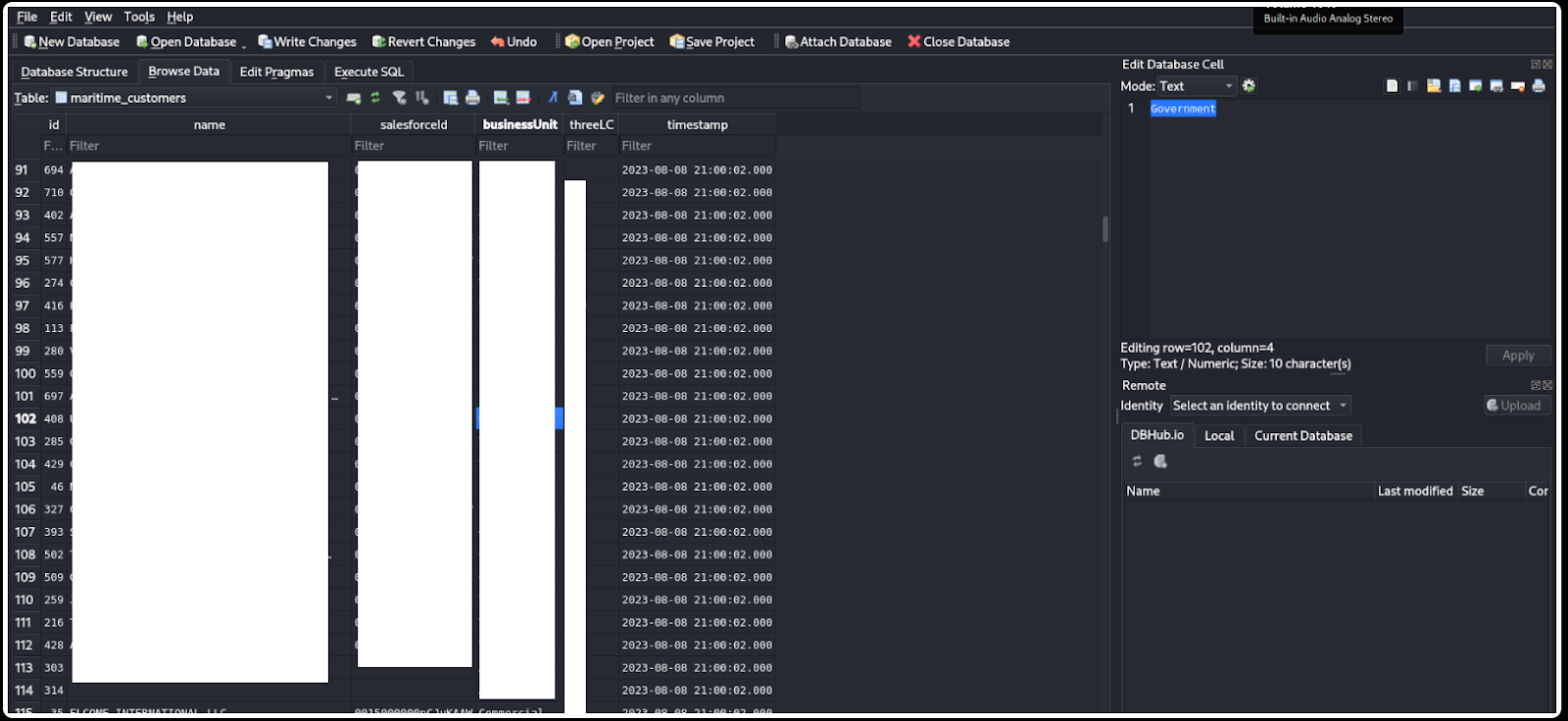
Moreover, the screenshots suggest that the data is being sold on the dark web. After a careful examination of the screenshots, the intrusion appears to be a PostgreSQL table dump, which contains the following information:
- Maritime customers (account data, such as corporate clients across oil and gas, cruise lines, government agencies, etc.)
- Maritime customer mapping (a linking or mapping table to connect customer records across various databases)
- User credential table, with full names, email addresses, phone numbers, postal addresses, and authentication data for employees, partners, or customers. Some of this data is linked to government entities. Passwords appear to be hashed.
- Starlink Contracts/Services database, showing which customers (shipping/yachts) have Starlink connectivity, who manages them, and service status. This contains the full names of the employee account managers.
The DarkForums user, who is obviously the attacker, posted the following description of the data breach:
Selling over 70 credentials used by Anuvu for different services, mainly AWS and Postgres databases for their infrastructure. Also included the database of their clients and customers, logs, etc. They work mainly with airlines, maritime companies and whatnot. I haven't tried all the credentials yet, there is too many angles to investigate.
From DarkWeb Markets to Potential Wide-Scale Fraud
The attacker said something that stands out in their message, “There is too many angles to investigate.” That is because the data breach itself is a ripple effect, aimed at causing waves for all the parties registered in the PostgreSQL data set.
At this stage, a threat actor can weaponize the information from the data breach by using real names and email addresses to craft highly convincing spear-phishing emails aimed at Anuvu employees, clients, or partners.
Moreover, if even one business email account is compromised, it can become a launchpad for impersonation attacks, since anything sent from that address will appear trusted and authentic.
Let’s take this further. Since major clients such as Carnival, Norwegian Cruise Line, Petrobras, and USCG projects are not only included in the data breach but are also publicly known to use Anuvu’s connectivity services, attackers can map the company’s customer base and direct their efforts at high-value targets.
Databases of this nature tie together a company’s operational infrastructure, effectively creating a roadmap of all the people and systems involved. For threat actors, this offers clear clues about where to probe for weaknesses and opportunities for abuse.