iBUYPOWER is the new target of the ransomware gang Lynx

Yesterday, the double extortion ransomware gang Lynx attacked iBUYPOWER, a California company that has designed and manufactured custom and ready‑made gaming desktops and laptops since 1999, making them a legacy player in the gaming PC space.
According to Lynx’s Tor site, which operates as a news bulletin to publicly inform about their latest targets, the group encrypted an undisclosed number of files belonging to iBUYPOWER, and categorized them as “Confidential” until the company satisfies the ransom demands. The group plans to leak the files to the public in 2 days.
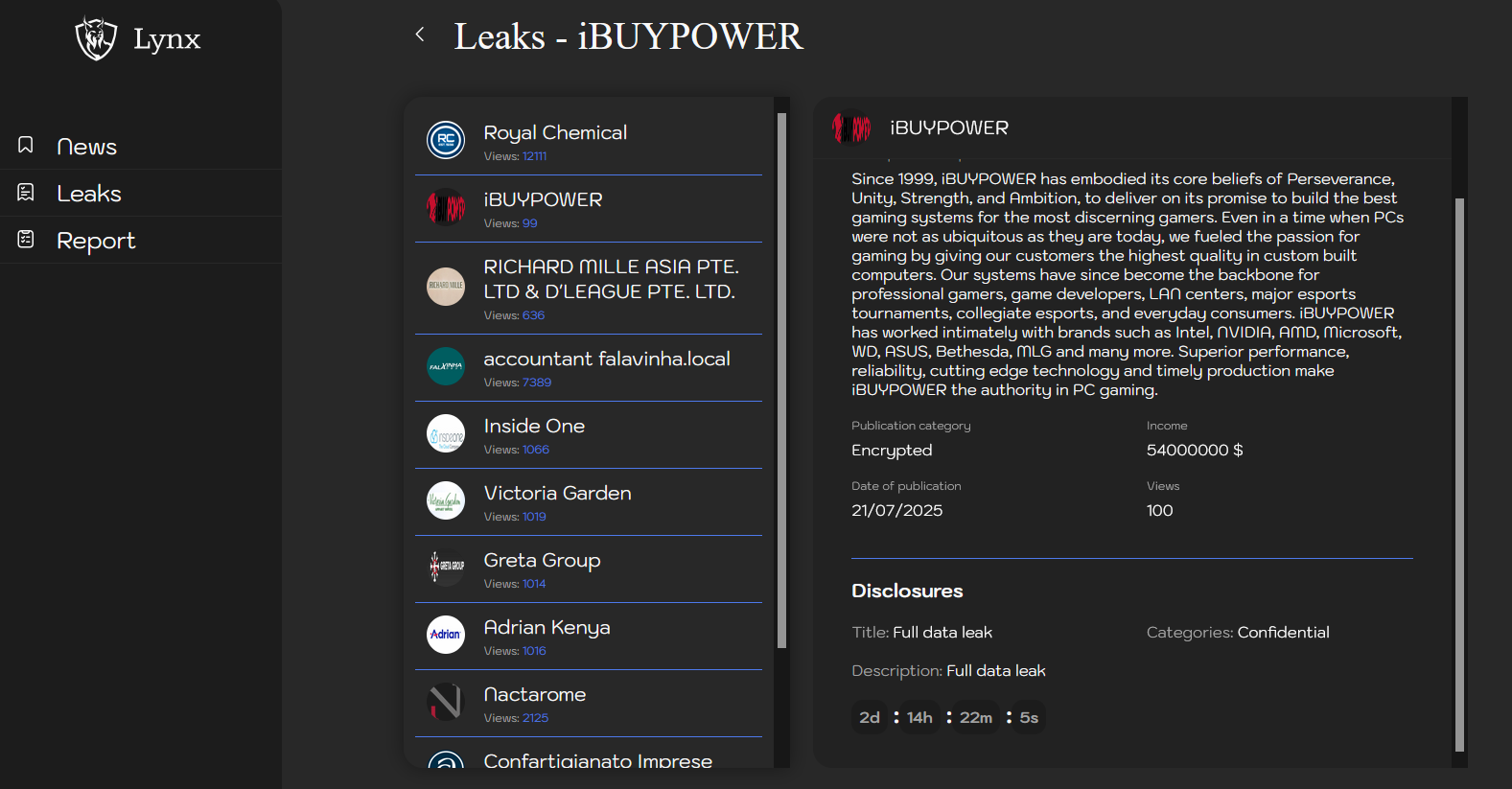
Lynx has not published any documents providing public proof of the attack. However, based on a review of the group’s previous campaigns, it is reasonable to deduce that an intrusion occurred. It is not uncommon for ransomware groups to withhold evidence of breaches; their reasoning is their own.
Lynx, Tactics at a Glance
Lynx first appeared on the radar in July 2024 and is considered a rebranded successor to the INC ransomware strain, since it shares up to 70% of its code, although its relationship to the ransomware strain is partially disputed.
The group operates an RaaS model (Ransomware-as-a-Service), which, like other ransomware groups operating under similar models, offers other cybercrime individuals and groups the opportunity to essentially rent the group’s ransomware toolkit to carry out attacks in exchange for a share of the profits.
This allows the core group to avoid constantly searching for new targets, as they receive 20–30% of each ransom payment collected by affiliates, funds often used to maintain the malware and infrastructure. The rest is pocketed.
These individuals and groups become more like clients or partners who are allowed to use the malware or become vetted and recruited in some way. They may be tasked with establishing the initial access of targets, which may come in the form of phishing, exploits, or purchasing credentials from illicit data brokers.
After gaining access to weakly protected systems, affiliates may proceed to launch the ransomware payload, exfiltrate sensitive data, and negotiate with victims over payment.
Using this structure, Lynx provides the backend infrastructure, which also includes the payment systems, and publishes the stolen data if victims refuse to pay or miss the deadline.
Lynx Reveals the Group’s Policies and Motives
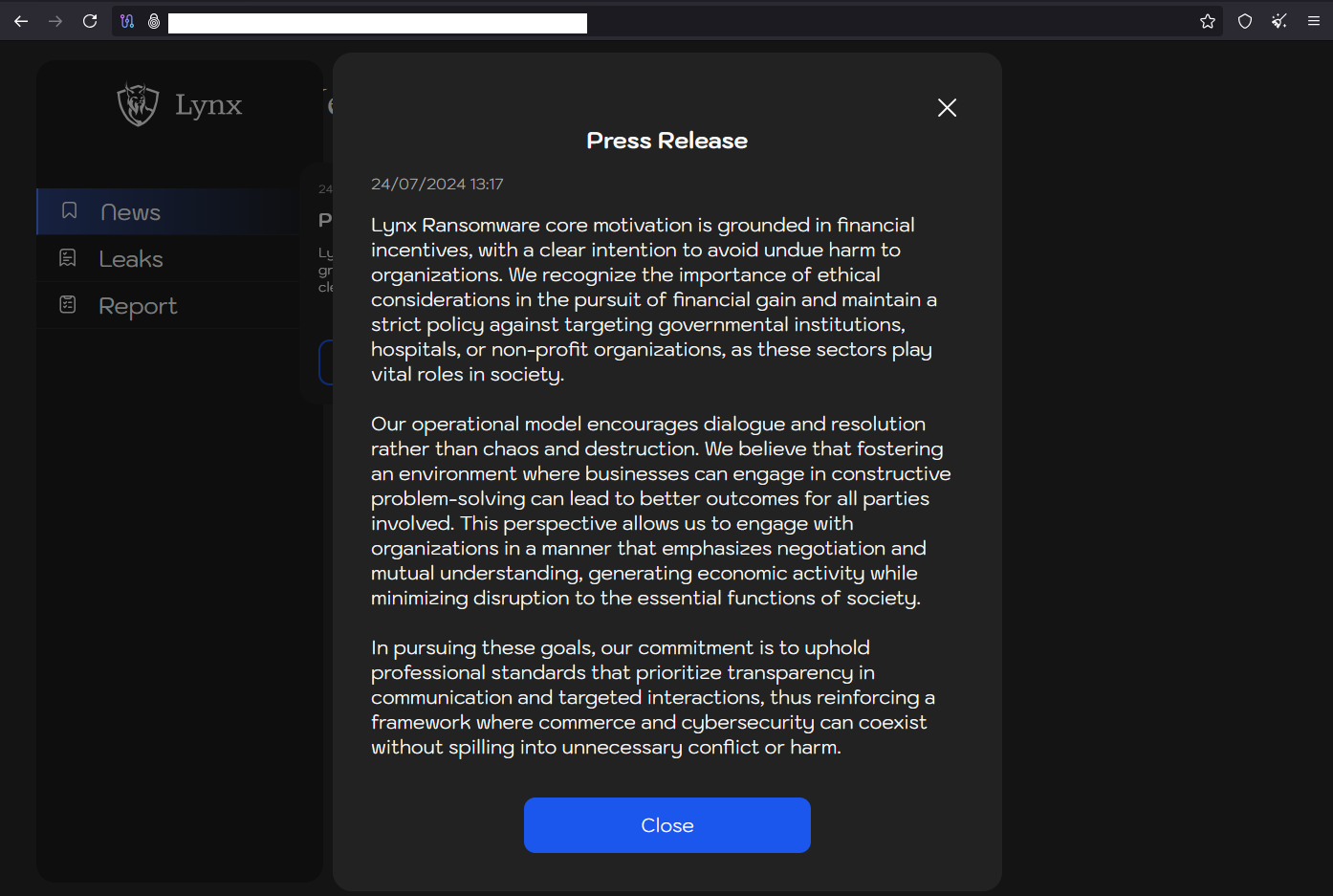
On 07/24/2024, Lynx published the group’s modus operandi on their Tor site, outlining their goals, which seem interesting since it outlines the group’s core policy against aiming their attacks at “governmental institutions, hospitals, or non-profit organizations”. In their own words:
“Lynx Ransomware core motivation is grounded in financial incentives, with a clear intention to avoid undue harm to organizations. We recognize the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy against targeting governmental institutions, hospitals, or non-profit organizations, as these sectors play vital roles in society.
Our operational model encourages dialogue and resolution rather than chaos and destruction. We believe that fostering an environment where businesses can engage in constructive problem-solving can lead to better outcomes for all parties involved. This perspective allows us to engage with organizations in a manner that emphasizes negotiation and mutual understanding, generating economic activity while minimizing disruption to the essential functions of society.
In pursuing these goals, our commitment is to uphold professional standards that prioritize transparency in communication and targeted interactions, thus reinforcing a framework where commerce and cybersecurity can coexist without spilling into unnecessary conflict or harm.”