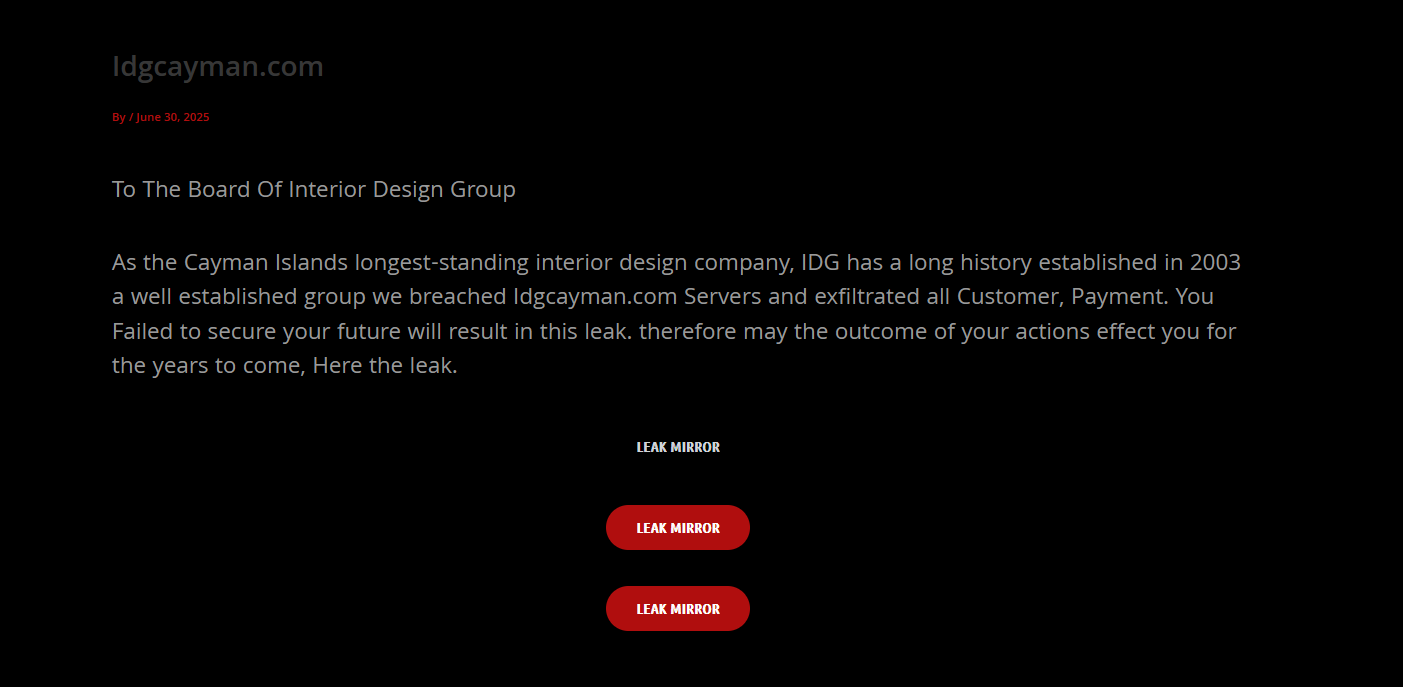
IDG Cayman Impacted by Ransomware Gang, FSociety

On June 30th, the Board of Interior Design Group in the Cayman Islands was hit by the ransomware gang known as FSociety, which also goes by the alias Flocker. However, the attack was only discovered yesterday.
IDG Interior Design Group, founded in 2003 in the Cayman Islands, specializes in luxury interior design, architecture, and high-end home furnishings. The company was named Gold winner for Best of Cayman Islands 2024, as well as the Innovative Luxury Interior Design Boutique 2024 by LuxLife Magazine.
FSociety published three leak mirrors on their Tor site, using the cloud-based file storage site Mega Drive, each containing a cache of exfiltrated data downloaded from the company’s compromised servers.
Also on their site was what appears to be a follow-up ransom message highlighting the company’s failure to meet the attacker’s demands.
Who is FSociety?
The group operates mostly as a Ransomware-as-a-Service outfit, offering their affiliates the ransomware tools, like custom payloads and backend infrastructure to carry out attacks, which increases the overall stolen revenue of the actors involved.
The group made its first appearance ostensibly in the Spring of 2024, following the detection of its unique malware strain, Flocker. The timing of their emergence is interesting since it coincided with the collapse or breaking up of major ransomware groups on the scene at the time, like Conti, REvil, and Hive.
Inside the Data Leak
Although the Mega Drive only contains a total of 104 files, 45.7 MB in size, it contains a wealth of financial data, including vendors, client information, payments, invoices, profits, losses, etc.
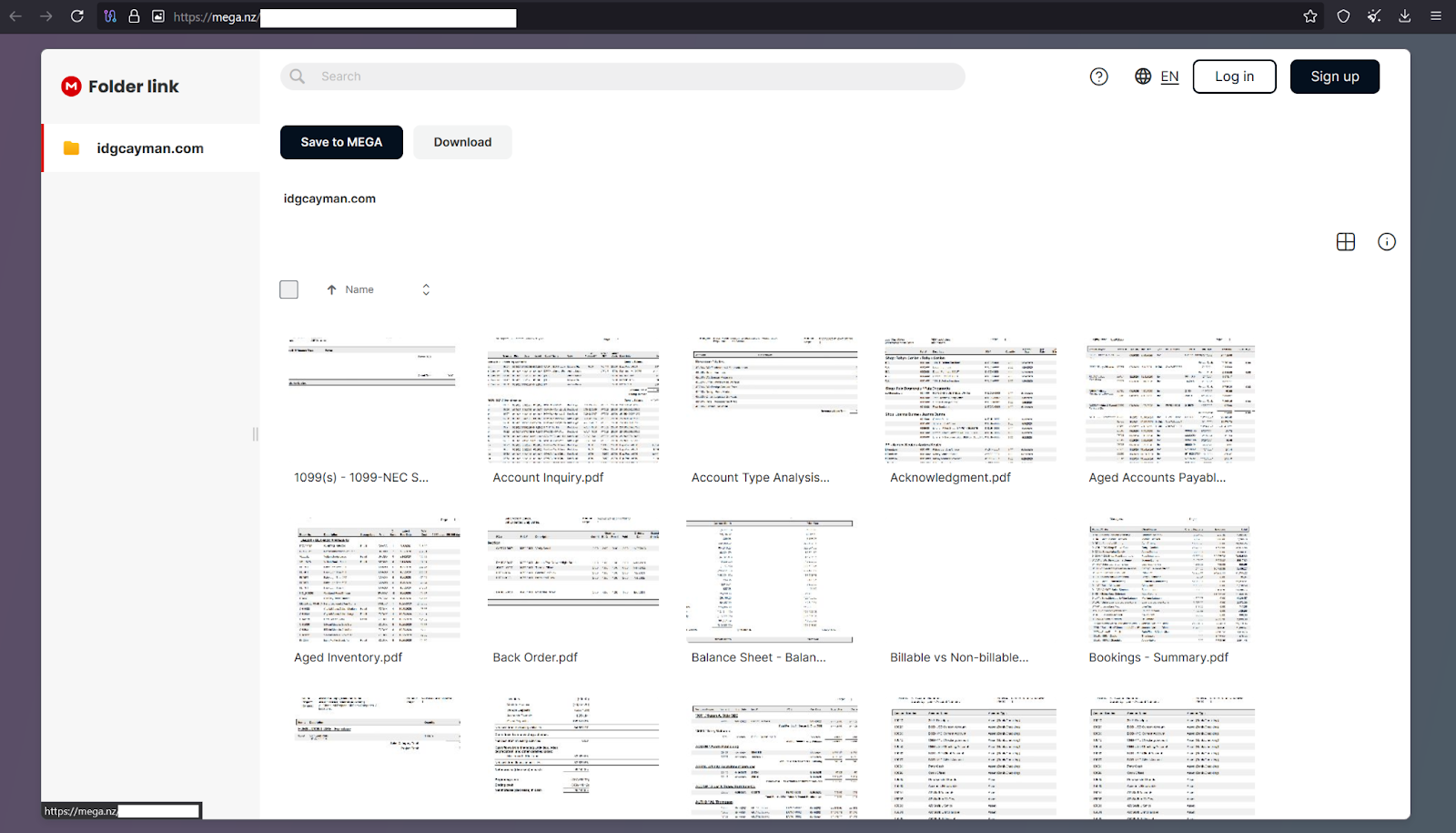
Arguably, among the trove of financial records, there’s very little damaging personal identifying information compared to most ransomware and data extortion attacks. It could be ascertained that this is part of the reason why the company declined to pay the ransom.
Perhaps, the most valuable information contained in the leaked files is in their financial infrastructure, as well as identifiable vendors and clients. The leak can be thought of as a cache of receipts, which a threat actor skilled in corporate espionage could analyze and possibly undermine the company’s trade secrets by selling the information to competitors.
Conversely, it seems most RaaS groups that only have a single trick up their sleeve don’t chase money in this fashion; when the time it would take to put in an additional operation involving corporate espionage, they can merely target other unsuspecting companies in the hope of a quick payout.