KillSec Leaks Royal Saudi Air Force F-15 Fighter Jet Documents

According to the ransomware gang’s Tor site, they claim to have compromised systems belonging to the Royal Saudi Air Force (RSAF) under the Ministry of Defense. The group initially released portions of the dataset as samples and listed the full leak for sale at €350,000.
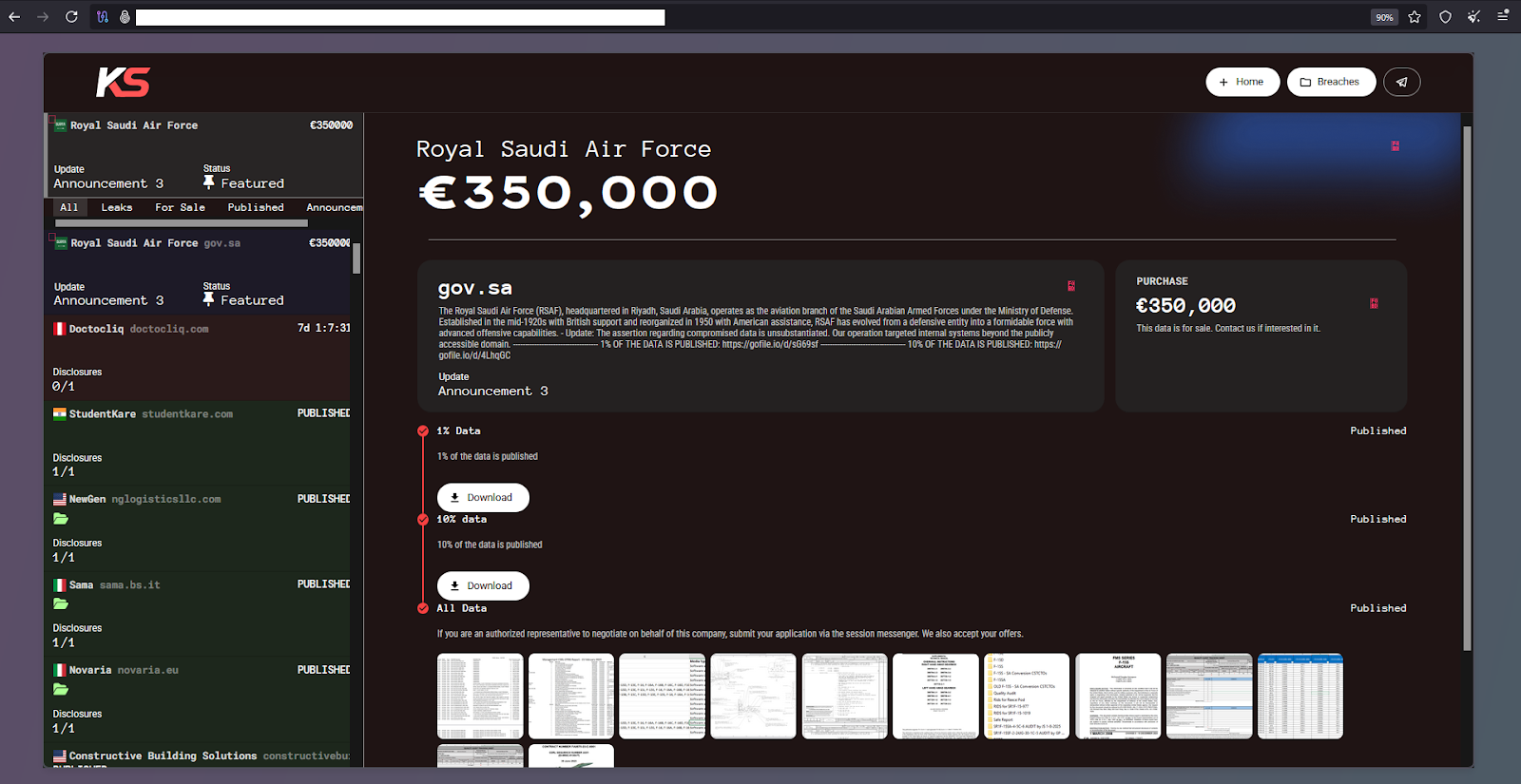
The group did not disclose how they breached RSAF servers; however, one of the 12 uploaded screenshots, a Windows folder tree, suggests the attack was ostensibly carried out via Remote Desktop Protocol (RDP).
While the download links for smaller samples appear to have been removed, a large sample appears available, totaling 9.1 GB in the form of a 7zip archive titled Royal Saudi Air Force.7z. Its creation or last modified date is April 2, 2025, at 6:43 AM.
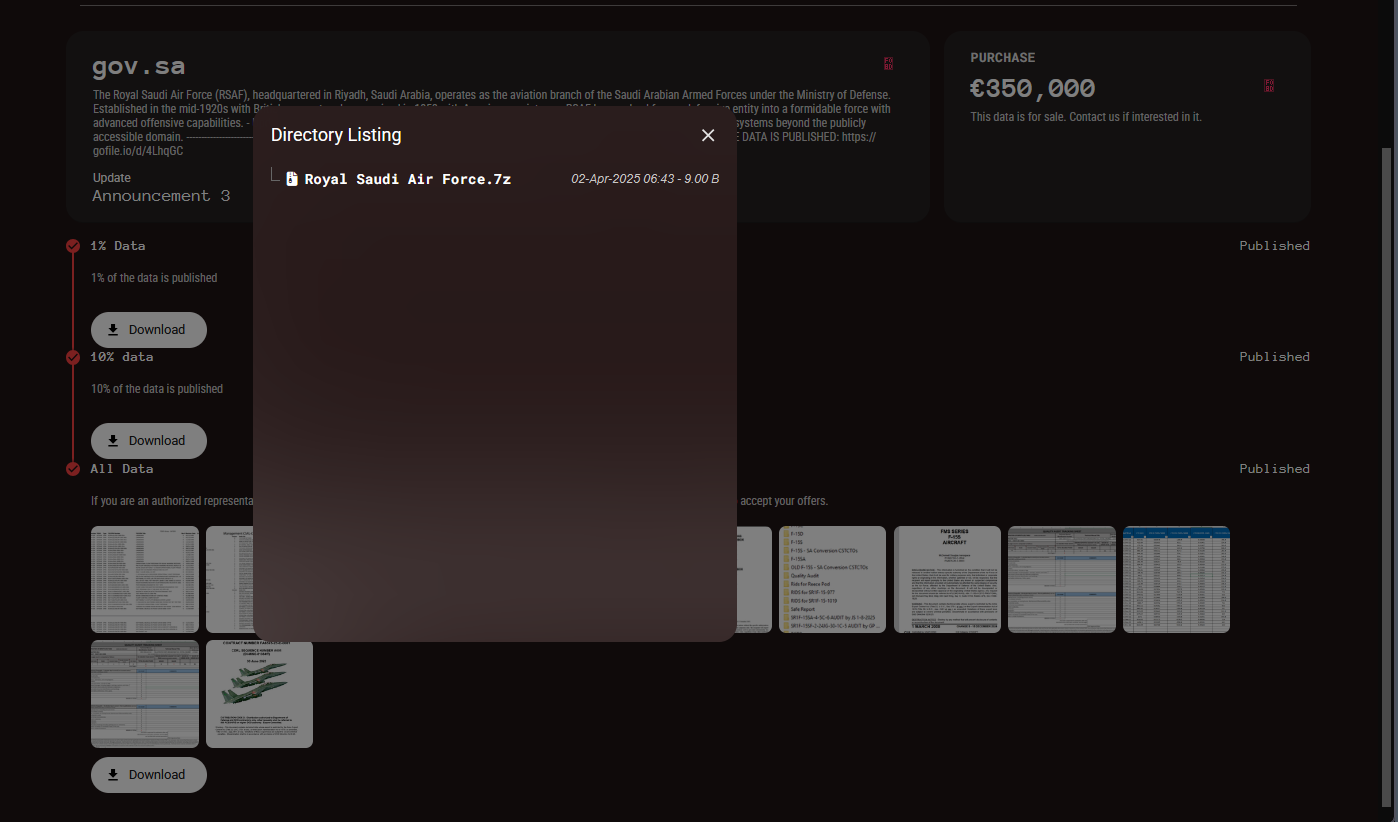
The screenshots show a mix of technical manuals, an engineering drawing, quality assurance audits, and software inventories linked to the F-15 fighter program, including aircraft operated by the Royal Saudi Air Force. One screenshot shows a highly detailed technical blueprint or engineering drawing of a structural component of the F-15 airframe.
Collectively, the material exposes subsystem-level details that could potentially aid in reverse engineering or inform adversaries about the jet’s sustainment and vulnerabilities.
From the screenshots alone, the following information was exposed:
- An Engineering drawing and repair instructions, showing how structural parts are maintained
- Software and program inventories
- Technical manuals and job guides, showing instructions for working on systems like electrical power, gearboxes, and fuel systems.
- Quality control audits for Air Force procedure compliance
- Operations data in the form of spreadsheets
- Library catalogs, showing indexes of software and technical orders, some marked as classified and tied to Saudi F-15 internally.
- File directories, showing a folder structure.
Who is KillSec
KillSec, also known as KillSecurity, is a self-described “prominent hacktivist group” that claims to have formed in 2023 and surfaced publicly later that year. The group presents itself as mixing disruption with digital activism, though the phrasing “operating in the cyber realm” already feels self-evident and redundant.
Despite projecting a hacktivist identity loosely aligned with Anonymous-style activism, KillSec’s actual choice of targets resembles that of typical cybercriminal groups and lacks clear political motives.
While they describe themselves as embodying “the complexities of modern cyber warfare, blending elements of activism with the darker facets of hacking culture,” their record makes their true motive apparent — anything but ideologically driven activism.
By mid-2024, they launched a Ransomware-as-a-Service (RaaS) model, complete with custom locker tools such as KillSecurity 2.0 and 3.0. The rest is history. The group victimized healthcare and medicine sectors across countries like India, Vietnam, and Belgium. A threat intelligence profile noted that approximately 20% of the group’s attacks have targeted the healthcare sector.
Most of the material carries export-control warnings (ITAR/EAR) and some portions are labeled Classified or Controlled Unclassified Information (CUI). Even unclassified content is sensitive because it reveals how the aircraft is maintained, what software it runs, and how fleets are managed.