Myrtue Medical Center Hit by Data Extortion Gang

Discovered yesterday, the data extortion gang known as World Leaks allegedly claimed another victim in the healthcare sector, Myrtue Medical Center, located in Harlan, Iowa. This marks 3 victims targeted in the healthcare industry.
At this time, little is known about the nature of the attack beyond the ransom note left by the group and the limited information available from their onion site on the dark web.
Dear [VICTIM],
We hope this message finds you well. We are writing to inform you of a serious matter concerning your company's data security. Our team has obtained a copy of your data, which is currently in our possession.
We understand the sensitivity and importance of this information, and we are reaching out to give you an opportunity to address this situation directly. If we do not hear from you by 7 days, we will be compelled to publish the data on our data leak site.
We strongly encourage you to contact us as soon as possible to discuss this matter further. Our intention is to resolve this issue amicably and avoid any potential harm to your organization.
Please reach out to us at your earliest convenience to discuss the next steps.
1) Download and run Tor Browser from https://www.torproject.org/download/
2) Navigate to a website: https://[chat link].onion
3) Log in using credentials: [random string:random string]
Sincerely,
World Leaks
[Onion link redacted]
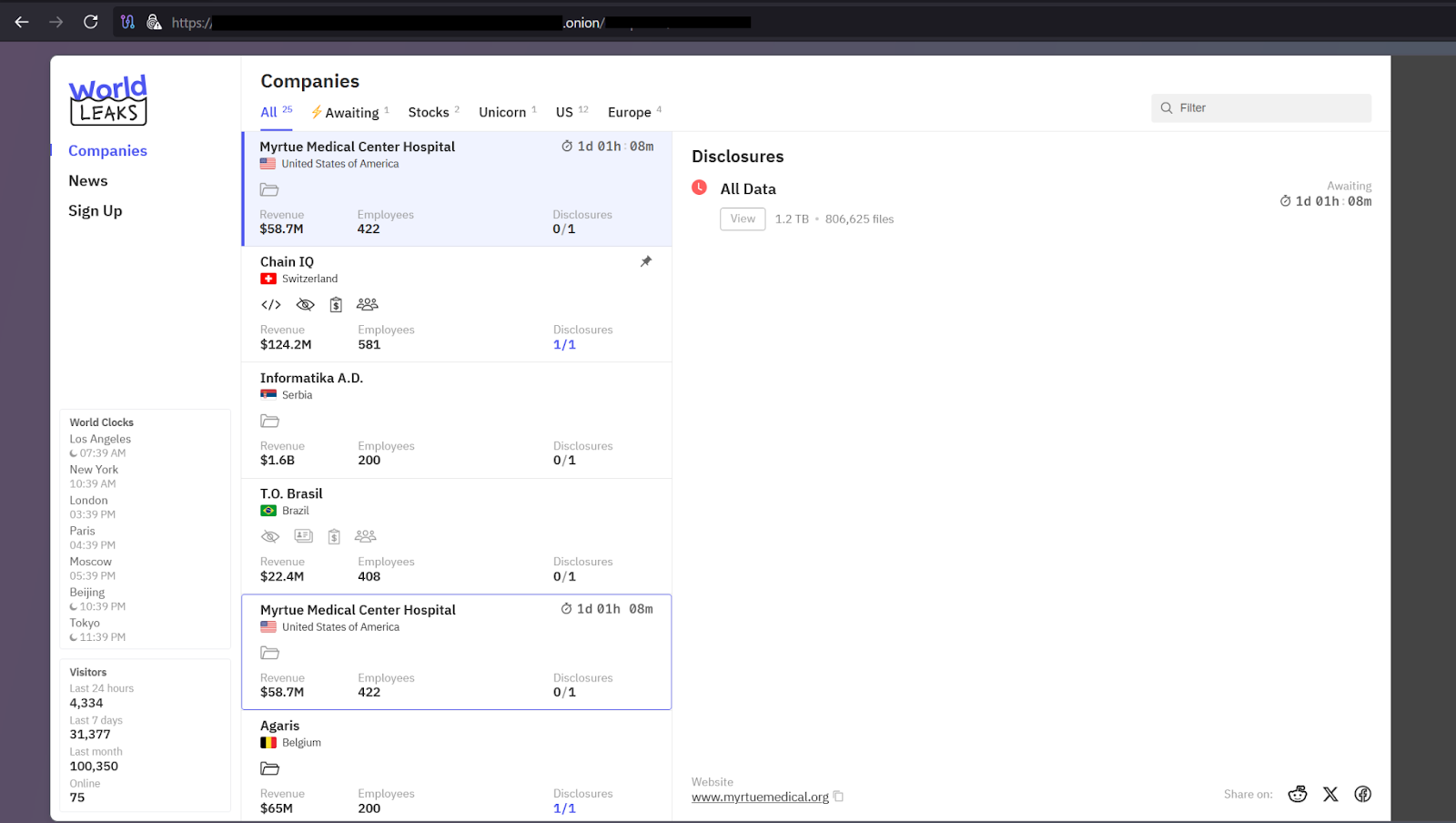
According to the World Group’s official onion site, the data siphoned from Myrtue Hospital totals 1.2 TB and consists of 806,625 files. As of this writing, the data has not been disclosed. The victim has 1 day, 1 hour, and 8 minutes remaining to pay the ransom or risk the exposure of their confidential records.
The extortionist’s site also references two previously attacked U.S.-based healthcare companies, Freeman Healthcare and Lake Region Healthcare, whose leaked files total 259.801 GB and 234,156 files combined.
Furthermore, a researcher with Leakd contacted the Myrtue Medical Center to learn more about the nature of the data breach, but the hospital declined to comment.
Identifying World Leaks
While using ransom threats to shake down companies is the status quo of most traditional ransomware gangs, the approach is more nuanced in the model used by this threat actor group, since their modus operandi involves silently infiltrating systems and exfiltrating the data in the hope of big illicit profits.
The extortion group World Leaks was formerly known as Hunters International, a ransomware-as-a-service operation. In a surprising move, the group decided to rebrand as World Leaks on January 1st and changed tactics by abandoning file encryption in favor of data theft and public shaming as extortion tactics.
This means the threat actor group has ostensibly discontinued locking companies out of their systems, opting instead to hold the exfiltrated data hostage, threatening to release it if the ransom isn’t paid by a set deadline.
Lastly, the way this group operates creates the proverbial heads of Hydra. By distributing data exfiltration tools to their affiliates, any of them can carry out attacks under the World Leaks banner. This tactic actually helps obscure threat attribution and complicates efforts to trace and unravel the complex layers of anonymity that bad actors use to hide behind.