Rhysida Ransomware Leaks Alascom Data, Demands $608K Ransom
Yesterday, the ransomware gang known as Rhysida leaked an undetermined amount of data from Alascom Srl, an Italian IT and industrial automation company based in Milan that provides system integration, IoT, robotics, and smart logistics solutions.
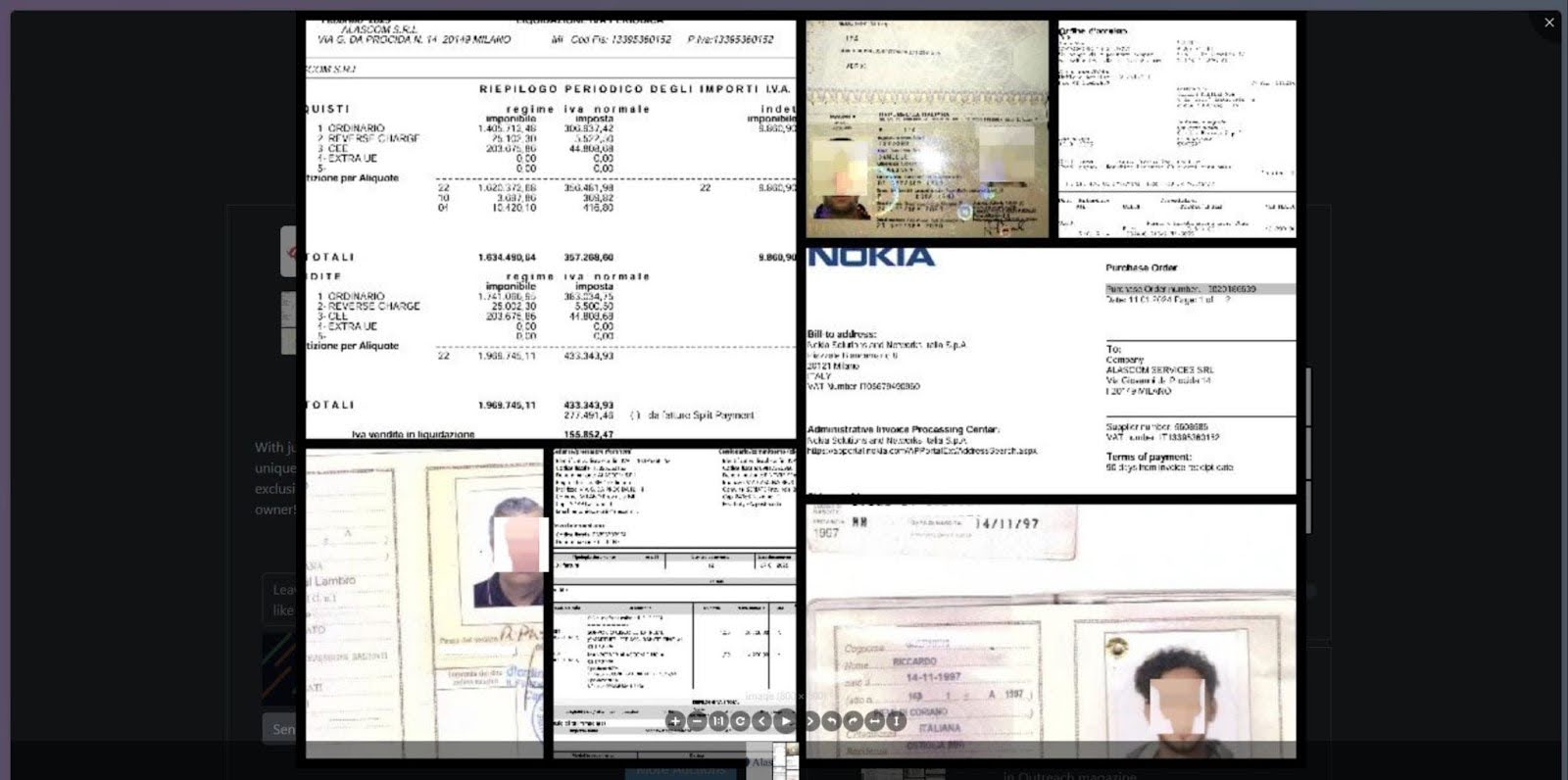
Among the screenshots shared as proof of the data exfiltration appear to be personal identifiable information (PII) such as passport and other identification documents, containing names, addresses, phone numbers, birth dates, along with various financial information.
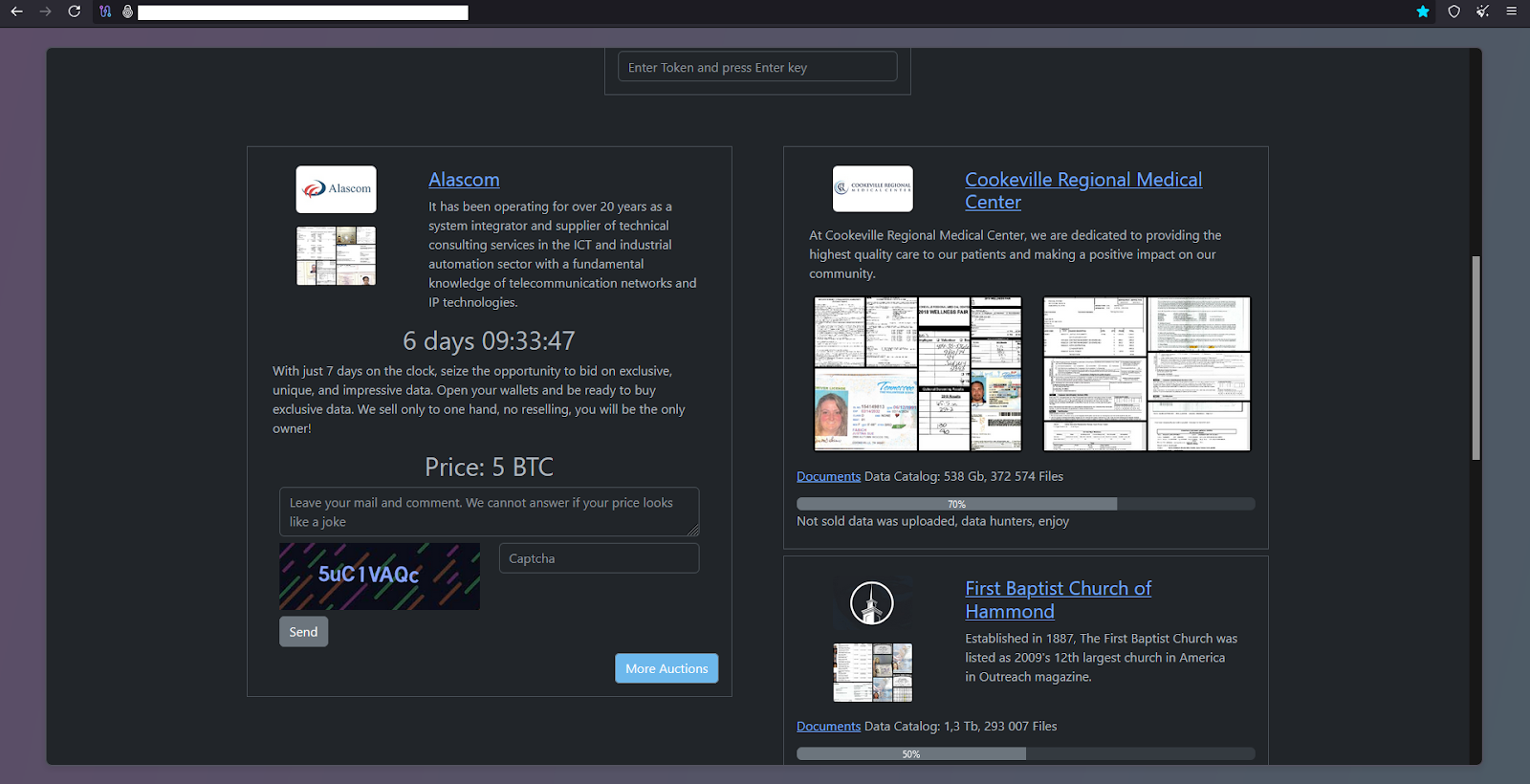
Rhysida operates by putting the exfiltrated data up for auction, allowing both the public and the victims to place their best offers on the value of the data. At the time Rhysida published news of the leak, they posted:
“With just 7 days on the clock, seize the opportunity to bid on exclusive, unique, and impressive data. Open your wallets and be ready to buy exclusive data. We sell only to one hand, no reselling, you will be the only owner!”
According to the countdown timer on Rhysida’s leak site on Tor, the gang has given the company 6 days to pay a ransom of $608,237 USD before they release the exfiltrated data to the public.
Financial Abuse
Leaked purchase orders often end up being abused in a variety of ways, depending on the information they contain and the target’s industry. The most common financial abuse is invoice redirection fraud. This occurs when a leaked invoice is modified and sent to the purchasing company with altered payment instructions.
Attackers also compromise business emails and use stolen purchase order data to craft convincing phishing emails to suppliers, and also request payment to attacker-controlled accounts.
Additionally, attackers may impersonate vendors. Simply by posing as the supplier listed in the purchase order, they can request early or duplicate payments.
Threat actors are also in a position to engage in competitive intelligence and corporate espionage. Not only the kind of threat actors we imagine, but also when data breaches like these occur, it puts desperate or shady competitors in an unethical position. They can see negotiated prices, quantities, and terms that can be used to underbid or steal contracts.
Exfiltrated financial data also allows groups like Rhysida to map out the supply chain. By identifying the victim’s suppliers and partners, it reveals who the potential soft targets are for broader attacks, which encompasses more victims.
Proactive Defense
Falling ransom and data-extortion payouts have not deterred cybercriminals, who continue their efforts in the hope of securing a single payout from an intimidated victim. The money that might be paid to cybercriminals or to legal teams specializing in ransomware negotiation and remediation could instead be invested in hardening potential attack surfaces.
Patching and updating systems aggressively, along with ensuring that backups are stored offline in air-gapped systems for easy file recovery in the event of an attack, is a crucial element of remediation. Yet while companies focus on broadening their empires and making money, their cybersecurity posture all too often remains unguarded.
As a former threat actor myself, my mindset is, “If it’s connected to the internet, it is vulnerable.” This means it’s not a matter of if, but when a cybersecurity incident will occur. Attacks are inevitable, but how you prepare in advance can, and will, determine who wins and loses in the conflict.