Sensitive Data of Over 1 Million Patients Leaked from Russian Clinic

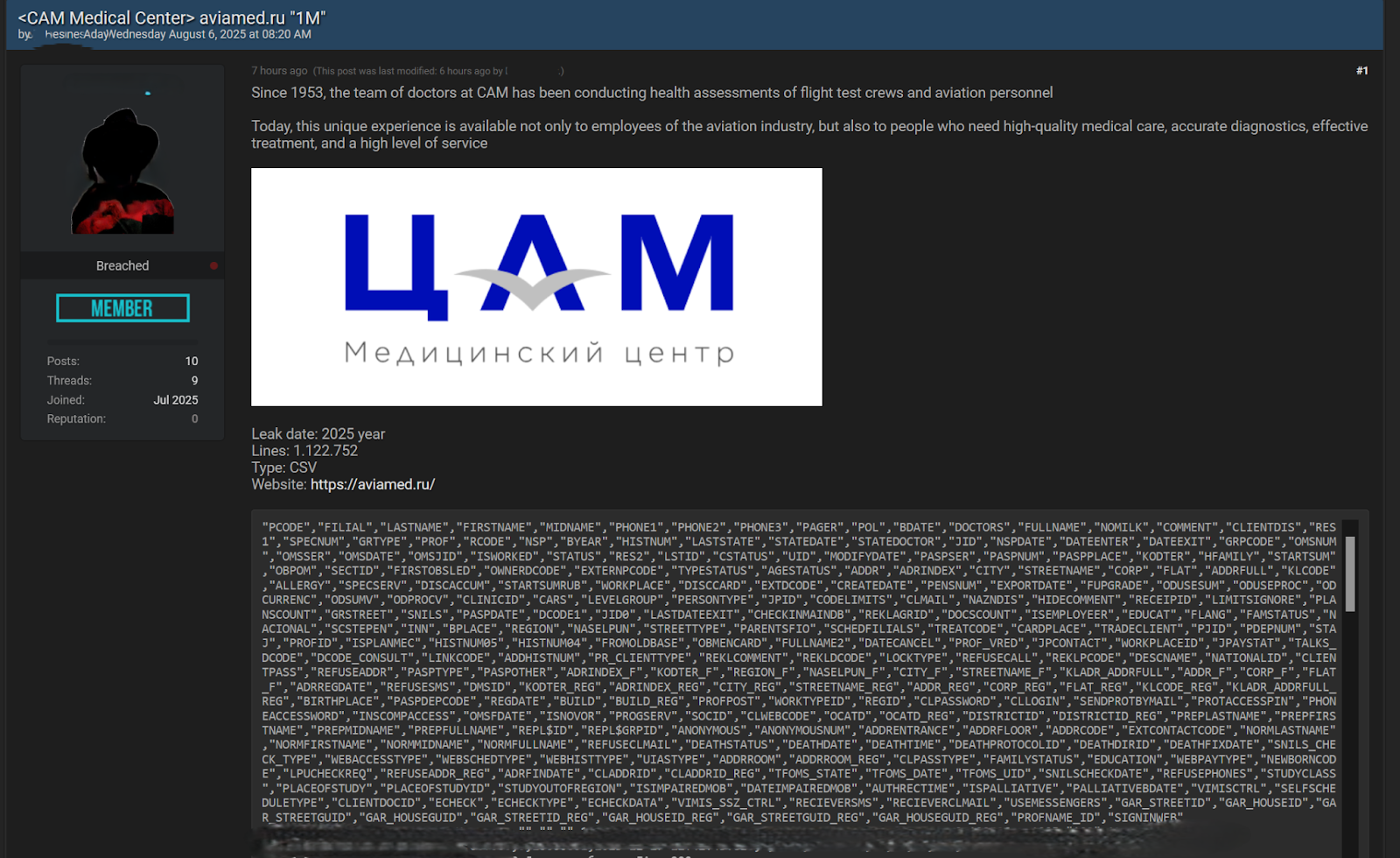
Today, a BreachForums member allegedly leaked a CSV file containing a sample of a massive dataset containing 1,122,752 individual records exfiltrated from a Russian electronic health record or patient management system from the Center for Aviation Medicine (CAM).
CAM’s primary clinic, based in Moscow, operates multiple branches in the region and is known for practicing multidisciplinary medicine specializing in aviation medical certification, diagnostics, and treatment, which caters to both aviation professionals and the general public.
The trove of data contains personal identifiable information (PII) such as full legal names, date of birth, Russian ID numbers (the equivalent of a social security number), Taxpayer ID numbers, passport numbers and their issuing agencies, phone numbers, email addresses, mailing addresses, and messaging preferences.
Breaking the Code
The leak goes deeper, as these are medical records containing an overwhelming amount of treatment and diagnostic data. Although the information is codified using a localized medical coding system, it isn’t globally standardized. However, a threat actor could easily cross-reference these records with other leaked medical data or online references to decode the contents of the CAM leak, which includes the following:
- Treating physician
- Patient medical history
- Conditions and service usage
- Palliative care flags
- Admission/discharge dates
- Insurance and health system data (i.e., Russian compulsory health insurance)
- Family status, nationality, academic status, place of employment, etc.
- Login credentials (usernames and email addresses used for email-based logins)
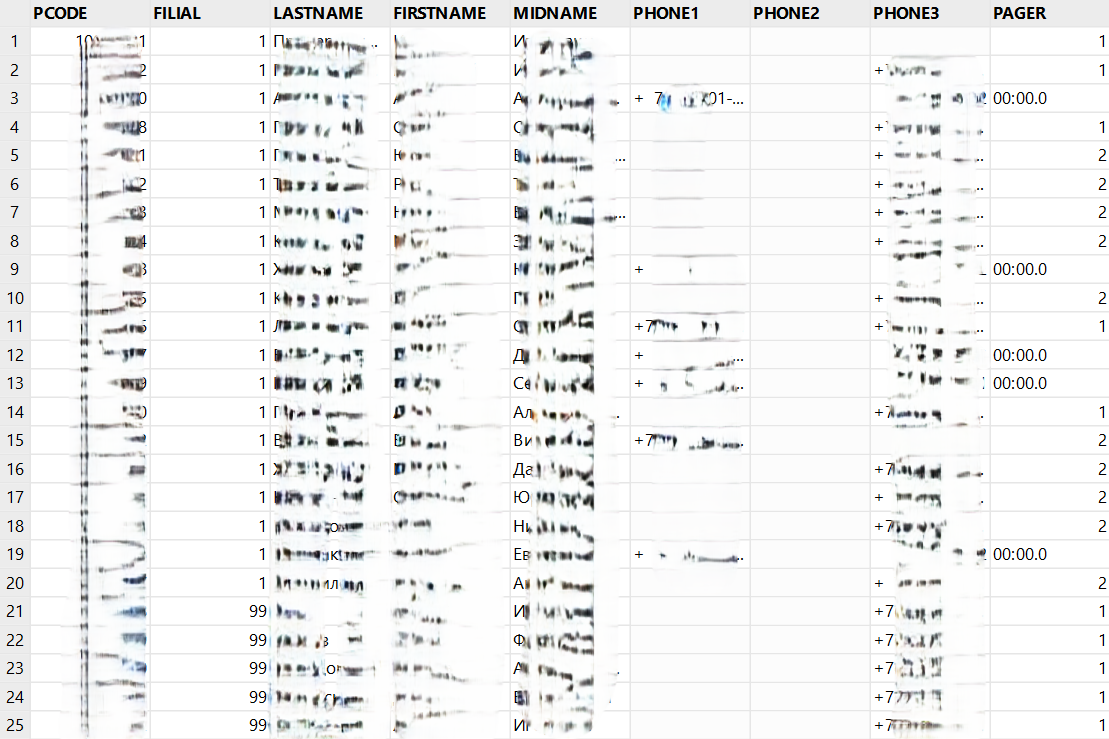
The image below is from the CSV dataset, showing PII, along with the branch code, and what appears to be a corresponding unique patient code, which we have obfuscated.
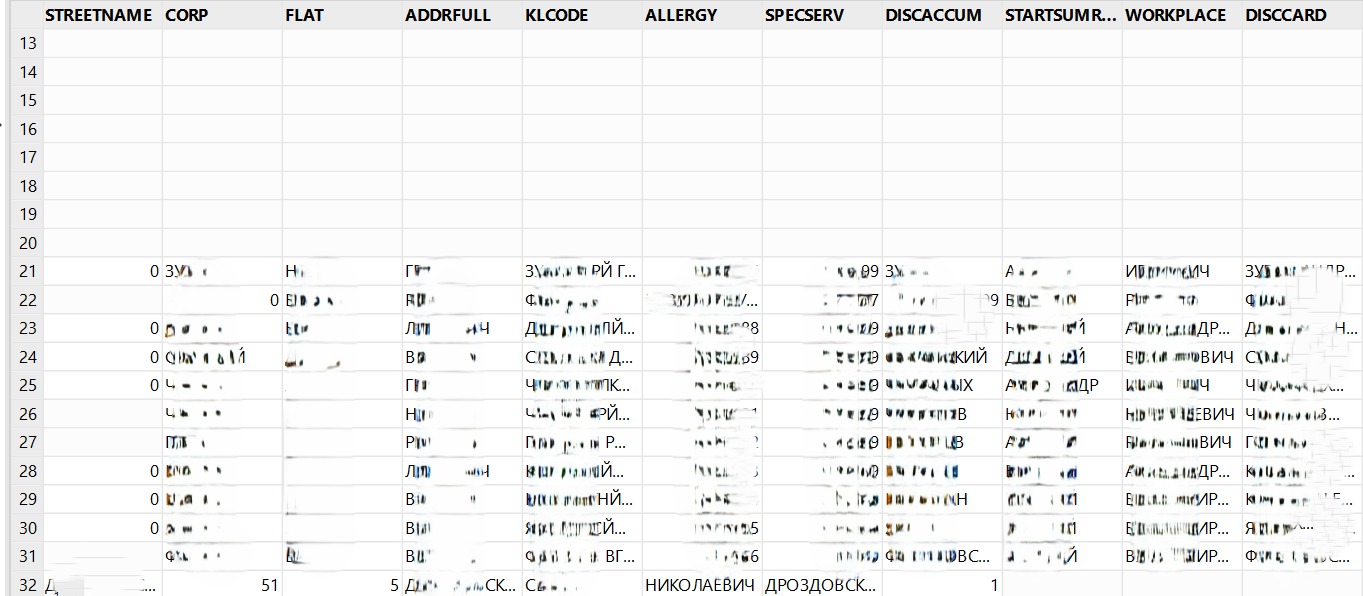
This CSV table exposes patients’ registered addresses, notes whether the patient lives in a flat or building block, and includes their corresponding address registry code. It also contains allergy classification codes, employer names, and other relevant information.
From Data Theft to Identity Theft
Due to the diversity of personal information contained in the dataset, the ramifications for identity theft are substantial. This isn’t your common run-of-the-mill PII leakage, so to put this into perspective, the following examples offer a glimpse into the ripple effect that could potentially follow.
- Forge identity documents such as passports, driver’s licenses, etc.
- Open bank accounts, take out loans, or conduct SIM swap attacks
- Apply for government benefits or medical services under a stolen identity
- Carry out long-term impersonation, especially as a member of the aviation industry.
While inconclusive, the damage can extend far beyond impersonation, as the leak contains patients’ mental and physical health status, prescription and procedure history, palliative care status, and diagnoses. Therefore, it is not uncommon for bad actors to acquire such information and use it for blackmail, or even go so far as to publicly shame, extort victims, or discredit and compromise government employees.
Healthcare Industry Attacks Remain Prominent
Last year, the FBI disclosed in the 2024 Internet Crime report that healthcare had the highest total of combined ransomware and data theft attacks across U.S. critical infrastructure industries, totaling 238 ransomware attacks and 206 data breach events in 2024.
That same year saw a total of 25.6 million hijacked healthcare records, which exposed over 115 million records. Furthermore, the average ransomware demand was around $5.7 million, while the average ransomware payouts from victims were around $900,000, according to the HIPAA Journal reporting for the years 2024-2025.
According to the Health-ISAC 2025 Cyber Threat Landscape Report, ransomware attacks are the most prominent cybersecurity threats aimed at the healthcare industry, with patient-level extortion emerging as a risk.
Verizon’s 2025 Data Breach Investigations Report noted that the healthcare sector saw 1,710 security incidents. From there, 1,542 incidents involved confirmed data breaches, with ransomware being a dominant aggressor.
Think about it. The downtime could potentially be life-threatening. Attacks can freeze emergency response systems, delay surgeries, and shut down intensive care units. Furthermore, leaking medical records can provoke lawsuits, regulatory penalties, and, of course, a stain on the company’s reputation. Many medical system infrastructures are outdated, unpatched, and inherently vulnerable.